DEW #127: SOC Visibility Triad, Feedback loops in detection, PowerShell detection ideation
In November 2006, Windows PowerShell was created. This made a lot of people very unhappy and has widely been regarded as a bad move
Welcome to Issue #127 of Detection Engineering Weekly!
✍️ Musings from the life of Zack in the last week
I’ve bought a subscription to Claude and I’ve really enjoyed using it over ChatGPT. I feel like it’s more concise in my asks, and it does a great job thinking like an engineer
Thank you all who reached out asking about sponsoring the newsletter. More on this soon but it looks like this is gonna be something I can do which is exciting :)
Growing this newsletter means more and more to me as I write. I’ve really REALLY enjoyed writing lately. I owe y’all several new issues of the Detection Field Manual, so stay tuned!
⏪ Check out last week’s issue if you’ve missed it!
💎 Detection Engineering Gem 💎
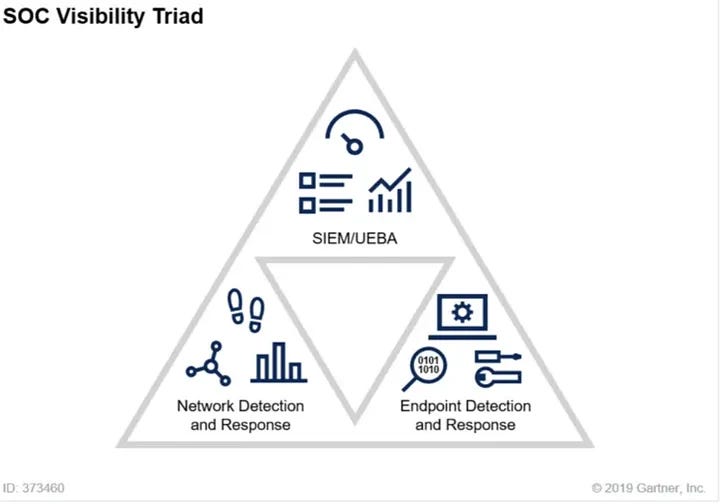
SOC Visibility Triad is Now A Quad — SOC Visibility Quad 2025 by Anton Chuvakin
When was the last time you read a blog series that started 10 years ago? Anton’s original post explained the “SOC visibility triad,” which contains core telemetry pillars that every security operations team needs to have visibility into. Remember, there is no rule without telemetry, so it’s essential to understand the highest-value telemetry in your network to write rules against. According to the original post linked above, the triad includes logs, network, and endpoints:
Arguably, every piece of technology in modern stacks can fit into one of these three buckets. And this makes sense: network and host deserve their own buckets, and SIEM can be a catch-all source as you lob whatever log source you can at it. However, many things changed between 2015 and 2020.
Anton revisited the triad in 2020, and although hyperscalers like AWS or GCP were skyrocketing in popularity, he did not add another leg to the triad. I think the spaces were nascent to threat actor activity at the time. In 2025, I don’t believe this is the case anymore!
Over the last five years, SaaS software has become an integral part of modern business, backed by hyperscalers. As a result, applications have become so complex that they require their own dedicated threat models. For example, understanding that Cloud platforms like AWS are operating systems themselves means they have sufficient complexity for threat actors to exploit, and the concept of Application Detection & Response (ADR) is entering the security lexicon.
So, the triad becomes a diamond, and application telemetry should now be part of your security operations umbrella. Now I hope Anton invites me on his podcast to debate this next :).
🔬 State of the Art
Malicious Encoded PowerShell: Detecting, Decoding & Modeling by Alex Teixeira
I am amazed by the complexity behind threat detection strategies, where detecting something seemingly simple becomes extremely difficult. This post is an excellent demonstration of that theme, where Teixeria discusses a detection opportunity of malicious PowerShell using the EncodedCommand argument. It’s one of those nuanced problems where a 1-hour interview discussion can focus solely on detecting malicious PowerShell usage.
He first starts with the basics of the technique: using the EncodedCommand parameter, which leverages base64 encoding to pass into the PowerShell executable. Encoding and decoding base64 in an executable should raise some eyebrows for security engineers, but it’s more common than we all think. Still, attackers use it for defense evasion and it can get difficult trying to differentiate benign and malicious usage.
The interesting aspect of this detection post is identifying all the variations of EncodedCommand flags. Teixeria calls out the parameter abbreviation “feature” of PowerShell, where you can pass all kinds of permutations, such as -en, -e, -encode and so forth. He builds some gnarly regular expressions to capture this, but keeps building out the complex edge cases until it feels, at least to me, untenable. The critical lesson under the 'Which logs to use?' section is that detection models should focus on detecting obfuscation, not encoding, as they can sometimes be conflated.
Echo Chambers — Feedback Loops in Detection Engineering by Nasreddine Bencherchali
Feedback is a gift. Acting on feedback is a way to utilize that gift in the best possible ways. But this post isn’t necessarily about getting feedback from your boss or loved ones, but rather, it’s about the diversity of feedback you receive on your detection rules. I love this concept because it frames detection, ideation, and maintenance under the threat of bias when you receive feedback.
In this post, Nas describes “The Echo Chamber Effect” of detection feedback. There’s nothing better than the dopamine hit of deploying a great detection rule, but will that dopamine and positive reinforcement keep that rule excellent in the long run? How about when you receive negative feedback, and you tune the rule so much that it’s brittle? What about chasing 100% MITRE coverage?
All of these feedback loops are pitfalls. Humans tend to focus on the immediate pain or pleasure of a response, which can lead us down a rabbit hole of confirmation bias. So, to combat the Echo chamber, Nas introduces several strategies to break out of it. These strategies are very similar to threat intelligence analysis, where analysts employ various techniques to challenge their biases and ensure their conclusions are sound.
GraphApiAuditEvents: The new Graph API Logs by Bert-Jan Pals
Microsoft recently released a GraphApiAuditEvents table for DefenderXDR, so if you are a customer of the product, you get this table for free. And by free, it doesn’t charge for ingestion or storage costs, which makes it a nice add-on for those looking to set up out-of-the-box alerting for Azure Entra. Pals compares this new table to the existing MicrosoftGraphActivityLogs for Sentinel. You receive the same event types and similar counts of log ingestion for the same events. However, GraphApiAuditEvents has fewer fields (19 compared to 33) and appears to be missing two critical fields related to Device and Session ID. Both of these are crucial for detecting credential stuffing and account takeover attacks, so you may need to incorporate other post-compromise mechanisms into your KQL rules to compensate.
Refinery raid by Nick Foulon
Have you ever wanted to set up an oil plant? I think I’d like that experience at least once in my life. I imagine the startup costs are pretty high, and you’d need lots of permits, permissions and there’s the whole thing about killing the planet you’d have to navigate, but I imagine the operational complexity is fascinating.
Jokes aside, doing security for an oil plant is the most interesting part for me. Luckily, Operational Technology (OT) security is becoming more mainstream for cybersecurity people, so it’s cool to see a blog post on how to setup and attack a Virtual Oil Plant. Foulon walks readers through setting up the Labshock Oil Plant environment, and it’s basically an Oil Refinery in a docker container.
It’s pretty terrifying that you can emulate connecting to a PLC and start turning pumps on and off. I hope operational environments aren’t this easy to attack!
Foulon ends the blog highlighting some of the critical vulnerabilities you explore during the lab, and sets readers up nicely for Part 2 with some defensive strategies.
☣️ Threat Landscape
Widespread Data Theft Targets Salesforce Instances via Salesloft Drift by Austin Larsen, Matt Lin, Tyler McLellan and Omar ElAhdan
The big threat landscape news from this past week involved a Salesforce integration and app company, Salesloft, suffering a data breach from UNC6395. According to Google’s Mandiant, UNC6395 compromised Salesloft and pivoted to their integrations with Salesforce. They exfiltrated shared secrets, such as OAuth app and secret keys, as well as other stored data, including cloud and API keys. They provide helpful hunting tips and indicators of compromise to help others investigate.
Amazon disrupts watering hole campaign by Russia’s APT29 by AWS
AWS Threat Intelligence released a blog detailing their disruption of Midnight Blizzard / APT29. This group is also known as Cozy Bear for those who want to harmonize. The team identified domain names used by APT29 that leveraged watering-hole techniques to redirect victims to attacker-controlled infrastructure, which was then used for performing phishing attacks utilizing Microsoft’s device code authentication flow.
Detecting and countering misuse of AI: August 2025 by Anthropic
This is a pretty crazy threat intelligence update from the security team at Anthropic. They uncovered a campaign by a threat actor who successfully ransomed and extorted 17 victims and used Claude to help them move through the attack chain. This is the excerpt from the Anthropic team:
The actor used AI to what we believe is an unprecedented degree. Claude Code was used to automate reconnaissance, harvesting victims’ credentials, and penetrating networks. Claude was allowed to make both tactical and strategic decisions, such as deciding which data to exfiltrate, and how to craft psychologically targeted extortion demands. Claude analyzed the exfiltrated financial data to determine appropriate ransom amounts, and generated visually alarming ransom notes that were displayed on victim machines.
Storm-0501’s evolving techniques lead to cloud-based ransomware by Microsoft Threat Intelligence (MSTIC)
Ransomware actors are becoming increasingly proficient in leveraging their access to pivot into cloud environments. In this post, MSTIC details an intrusion they helped respond to for Storm-0501. The group got access to a victim environment, elevated privileges, and then pivoted to several of their Azure tenants. They used AzureHound for reconnaissance and attack path mapping until they found a non-human identity with Global Admin access. They exfiltrated data from Azure storage accounts and deleted as much as possible from those same storage blobs.
🔗 Open Source
LLM powered credential stuffing tool. You point it at a login page and it’ll determine the login endpoint and it’ll try to brute force credentials to find valid accounts. You can use a locally hosted model and a Chromium browser and its smart enough to try to rotate several features to avoid bot protection mechanisms.
Agentity-com/mcp-audit-extension
This is a great project that proxies MCP client/server communication using a VSCode extension. Lots of MCP interactions operate within IDEs specifically, so logging there makes total sense. You can look at the calls to MCP servers and send it to a SIEM or logging infrastructure. Here are the fields it logs in JSON format.
mandiant/flare-floss/releases/tag/quantumstrand-beta1
Mandiant released a tool for malware analysts and reverse engineers that helps find, tag and present interesting strings in a binary sample. The README says they want to provide “deep context” around strings in a tree-like manner so you can circumnavigate the binary without losing track of why certain string values exist in a region of the code.
Run a full Windows OS directly in a docker container! This is a fun one because it lists out Windows OSes all the way back to Server 2003, which is a whopping 600 MB. This might be a fun one to run with threat emulation pipelines and for detection ideation.
IDA pro extension to optimize binary diffing. This is especially useful if you want to reverse engineer patches in operating systems and see where vulnerabilities were fixed and build payloads to exploit older versions. These are especially fun when you don’t have access to anything but the OS images.