Det. Eng. Weekly Issue #124 - The DEFCON hangover is real
Yall are tiring me just from all the posts and drunk texts
Welcome to Issue #124 of Detection Engineering Weekly!
⏪ Did you miss the previous issues? I'm sure you wouldn't, but JUST in case:
💎 Detection Engineering Gem 💎
Aren't AWS Cloud Investigations the same as On-Prem? - Part 1 (AWS EC2) by Chester Le Bron
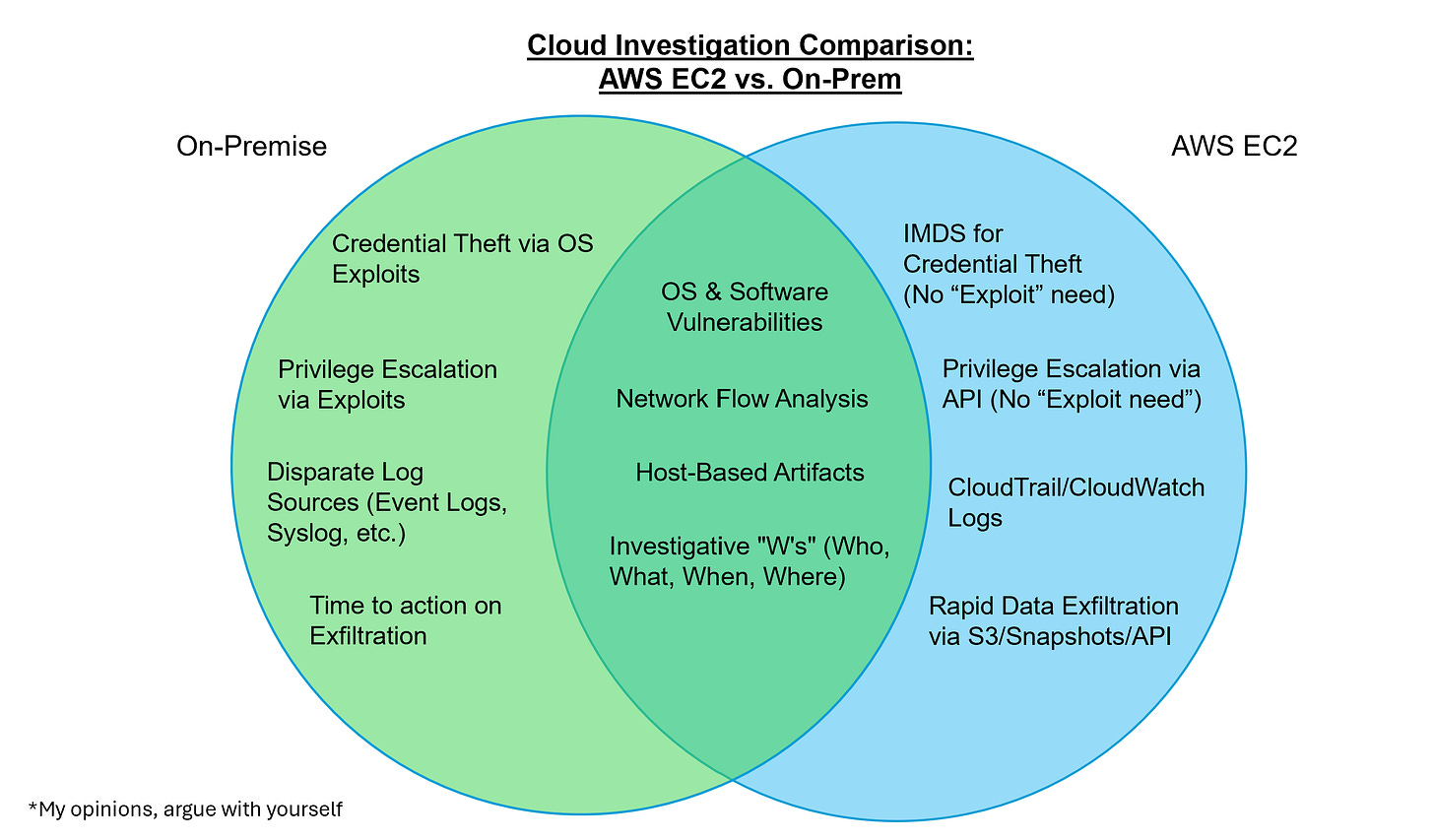
Le Bron is back, this time with a new mini series comparing and contrasting incident response investigations between on-premise and AWS environments! This is an excellent topic since hyperscalers (read: AWS, Azure, GCP) have become a regular part of business operations, particularly for software developers. Le Bron begins the blog by discussing the similarities between the two. These similarities are in the middle of the Venn diagram he built here:
And for the sake of the exercise, Le Bron only talks about compromise scenarios on EC2 instances. You'll want to look at how an attacker leverages exploits on vulnerabilities on the server or endpoint, examining network traffic to identify dropped malicious files, but the similarities stop there.
You now need to become an SME in the operating system called AWS and its core services, some of which (like IAM) could be considered its own OS due to their complexity.
This is a great way to frame the issue of cloud-based attacks, because it can be daunting to view AWS as an Operating System. It has its own peculiarities, management events (Kernel code), data events (log telemetry sources like network traffic), and privilege escalation paths that never touch the server itself. Le Bron calls this "the crossover", where once cloud credentials are stolen from the victim EC2 server, an attacker doesn't need to interact with the server anymore. They are attacking the "AWS operating system" itself, which can give them way more access to parts of your environment than the server.
🔬 State of the Art
Kali Linux & Containerization (Apple's Container) by Kali Linux
The Kali team posted a great tutorial on how to use Apple's new Containerization feature to run Kali natively on the latest version of macOS. You will need to be on their latest Tahoe or Sequoia releases. The interesting part here is how it's similar to Windows Subsystem for Linux, where macOS spawns a lightweight virtual machine to run the container and exposes APIs for the Containerization system to interact with the virtual machine and hypervisor.
It took me about 1 minute to get everything installed and Kali running. I guess I'm an ub3r hax0r now!
Building an AWS GuardDuty Alert Triage Agent by Dakota Riley
I've been on an AI SOC kick investigation lately, so Dakota's latest blog on building your own Alert Triage agent for GuardDuty had wicked good timing. GuardDuty is an AWS service that generates threat detection events in your environment, and it's notorious for being noisy. And as you've seen from some of my latest posts on AI SOC and automated triage, these agents are particularly good at closing out noisy alerts so you can focus on the potential true positives.
Dakota put this to the test with Pydantic, using several of their agentic options to build connectors to the AWS API for investigation, prompting the agent, and generating responses and mapping them to a clean API definition for the agent to use. He piped the alerts to Discord, as well as gave the ability to query alerts from Discord, and the agent performed its investigation and gave results with recommended next steps.
This goes to show that Agentic applications for security are becoming commoditized, and the startup cost of running your own isn't as hard as it was even six months ago.
Threat Hunting vs. Incident Response: What's the Difference? by Nima Bargestan
This is an introductory and beginner-friendly blog post on the differences between two core elements of Security Operations: threat hunting and incident response. Bargestan cleverly distilled the concepts down to two starting points: threat hunting is proactive, and incident response is reactive. They listed out the technical skill sets required for each role, but I also enjoyed how they included the soft skills required, which are often overlooked. You can be the most technical person in the world, but if you aren't calm and sturdy under pressure, then incident response probably isn't the right career path for you.
CTI Diaries — 1: Understanding Cyber Threat Intelligence by Deniz Topaloglu
I'm quite opinionated on how people define, use, and defend the term Cyber Threat Intelligence (CTI). It's a classic pitfall to think CTI means data: you download a feed of bad IP addresses, you feed those bad IP addresses into a system, and if you get a "hit," you block or alert. This is the poorest application of CTI if it's the only way you think it's useful.
Luckily, Topaloglu wrote this fantastic post about the benefits of a powerful CTI program. It does require expertise and an understanding of many security concepts. Still, the basic idea is that CTI analysts should collect, analyze, and disseminate information for downstream customers to make a decision with that data.
I love the section on "CTI Makes Risk Tangible", where they frame how a recent vulnerability is being exploited in the wild and threat actors are discussing how to use it. Lots of folks stop here, but in this hypothetical scenario, the CTI team takes it one step further and says, "you have two machines that are vulnerable to this specific CVE", which should elevate the urgency on patching those systems first.
Would You Know If Your EDR Logs Stopped Flowing Yesterday? by LogFiend
I love this topic from LogFiend because it's one of those unsexy but critically important parts of Detection Engineering. We spend so much time focusing on finding badness, as we should, and we look at the healthiness of our detections through the lens of coverage, rule count, and noisiness. According to LogFiend, we also should look at the healthiness of our log pipelines and data availability as part of this metric.
Detection Pipeline resiliency focuses on having a good inventory of what log sources should be sending telemetry to your EDR or SIEM, and detecting whether or not those log sources become unhealthy. This can range from botched deployments, changes in field structures, hosts losing connectivity, or simply the EDR agent crashing.
They recommend several ways to record the health of these pipelines, and surprise, surprise, they all look like site reliability and DevOps engineer methodologies!
☣️ Threat Landscape
This is an interesting vulnerability post from CISA. Basically, Microsoft released a patch for Hybrid Exchange environments that results in a privilege escalation from On-Prem Exchange to Cloud-hosted Exchange Online. The associated guidance from Microsoft had some interesting tidbits in their writeup, and my favorite was:
In this scenario, successfully exploiting the vulnerability could enable an attacker to escalate privileges within the organization's connected cloud environment without leaving easily detectable and auditable traces.
Now the question is: is it because most people can't afford the logging tier to get "detectable and auditable traces"?! Just kidding!
Leak Reveals the Workaday Lives of North Korean IT Scammers by Matt Burgess
It's rare to get a peek into Advanced Persistent Threat (APT) operations, primarily because Western countries sanction CRINK (China, Russia, Iran and North Korean) countries, and are firewalled off due to all kinds of national security concerns. So, when a researcher named "Styyk" reached out to Burgess to showcase some of their research on North Korean IT Worker activity, he got a deep dive into the logistical elements of their operations. Spreadsheets, metrics, a group manager, and front companies were all leaked in a trove of Google Drive, GitHub, email, and chat data.
Dissecting the CastleBot Malware-as-a-Service operation by Golo Mühr
Maybe I'm aging myself, but I do remember the days when downloading cracked software led to malware infections. But, in those days, they were resulting in infections via exploit kits, which were pieces of malware that exploited the browser itself to gain remote code execution. Browsers have become super resilient since then, and you don't read much about kits anymore.
This is why malware families like CastleBot are interesting. The same cracked or illegitimate software precursor still exists, but according to Mühr, it has a much different infection chain. For example, why exploit the browser when you can just have the user run the malware itself? CastleBot employs stagers, downloaders, and a main malware strain and has dropped everything from infostealers to Rhadamanthys.
Shedding Light on PoisonSeed's Phishing Kit by Efstratios Lontzetidis
PoisonSeed is an interesting phishing kit allegedly leveraged by actors in "The Com" (Wikipedia links to Scattered Spider here). It's interesting because it focuses on obtaining credentials for email infrastructure, which is then leveraged for follow-on phishing attacks. It's different because I typically associate phishing kits with harvesting bank or crypto credentials, or in the case of The Com, stealing corporate credentials for initial access. It looks like Lontzetidis obtained the phishing kit code and reversed its functionality, and also provided lots of domain IOCs for hunting.
From Drone Strike to File Recovery: Outsmarting a Nation State by Guy Barnhart-Magen, Brenton Morris
This post follows an incident response team’s response to a cybersecurity breach at a company that was ransomwared by a Nation State threat actor. It followed a drone strike from Israel on Iranian targets, and from what I can tell, implies that the victim was a result of a retaliatory strike by Iran.
The interesting parts about this story are that a) they believe it was a destructive attack disguised as ransomware and b) the threat actor is pretty bad at cryptographic operations. The responders managed to decrypt critical files for the victim using some good old fashion cryptoanalysis and binwalk!
🔗 Open Source
anthropics/claude-code-security-review
The Anthropic team released their open-source code security review that leverages Claude. You can add a GitHub action with your Claude key and it’ll review all your pull requests for well known vulnerabilities.
This is a neat threat emulation tool that generates ETW events for detection engineers to test all kinds of Windows attack scenarios. It uses a TUI interface and provides 18 different attacks, but it can also generate the exact Event Log or ETW event to help generate alerts.
trailofbits/mcp-context-protector
Really interesting security proxy that you wrap your MCP client/server connections around for AI guardrail usage. You can run it server side or client side, and has a cool quarantine feature to inspect quarantined security events and block or release them.
Node.js based middleware that you can use to shim file upload functions on your servers to check for malware. You can upload YARA rules for additional scanning, and it’ll do several enrichments on top of the upload such as MIME type scanning, allow listing for extensions and ZIP bomb detection.
Reverse proxy for TLS connections that you can use to generate client and server-side hashes a la JA4/JA4H. It can also route suspicious or honeypot traffic to Galah for generating LLM style honeypot responses based on the incoming traffic.