Det. Eng. Weekly Issue #123 - Mom said I couldn't go to hacker summer camp this year
*Insert 90s/00s kid angst while all my friends play four square/craps at the Aria*
Welcome to Issue #123 of Detection Engineering Weekly!
Some words of wisdom to all of you at Hacker Summer Camp this year
Hydrate
Introduce yourself to 3 people a day that you’ve never met and ask what they like about security
When you spot a fed make sure to yell out “I FOUND A FED” as loud as you can
⏪ Did you miss the previous issues? I'm sure you wouldn't, but JUST in case:
💎 Detection Engineering Gem 💎
SACR AI SOC Market Landscape For 2025 by Francis Odum and Rafal Kitab
It’s rare for me to link or reference market analysis work, but my friend Francis just did the industry and us detection engineers a massive favor by publishing this deep analysis on AI SOC companies. It fits so much of the criteria I look for with research posts: available for anyone to read, comprehensive, no marketing fluff and contains actionable insights that you can takeaway from the post.
I think we’ve all heard about these companies claiming to help reduce false positives and focus analysts and detection engineers on the complicated and nuanced investigations. The promise is that by leveraging Agentic architecture with pre-trained, hyper-optimized agents to do investigations on your behalf, you gain capacity and time back for your day-to-day. But, according to Francis, not all of these companies architect their solutions in the same way. There are two sections I want to point out that are super relevant for readers.
In this section, Francis and Kitab explore the four architectural flavors of AI SOC companies. Each company fell into these buckets in a number of ways.
The pure-play AI Triage agent triaging on your behalf
The AI Security “fabric” that connects all of your tools and serves almost as a SOAR 2.0
The co-pilot that augments your knowledge with quick prompting of internal and external knowledge bases
Browser-based or workflow capturing agents that encode your day-to-day into agentic workflows and become, as both Francis and Kitab put it, “digital twins”
I appreciate their assessment methodology here because it’s something we all can take back as a template for our vendor evaluations. Besides targeting traditional SOC and Detection metrics like MTTR and MTTD, they both recommend that buyers focus on flexibility in integrations, the ability to do some level of forensic analysis on artifacts, and novel threat detection.
It’s a long read if you want to do it in one go, but it’s a piece that I think serves itself well as reference material for when you have to eventually answer your boss’s question on whether we can use AI in the SOC :).
🔬 State of the Art
Lateral Movement – BitLocker by Pentest Laboratories (ipurple.team)
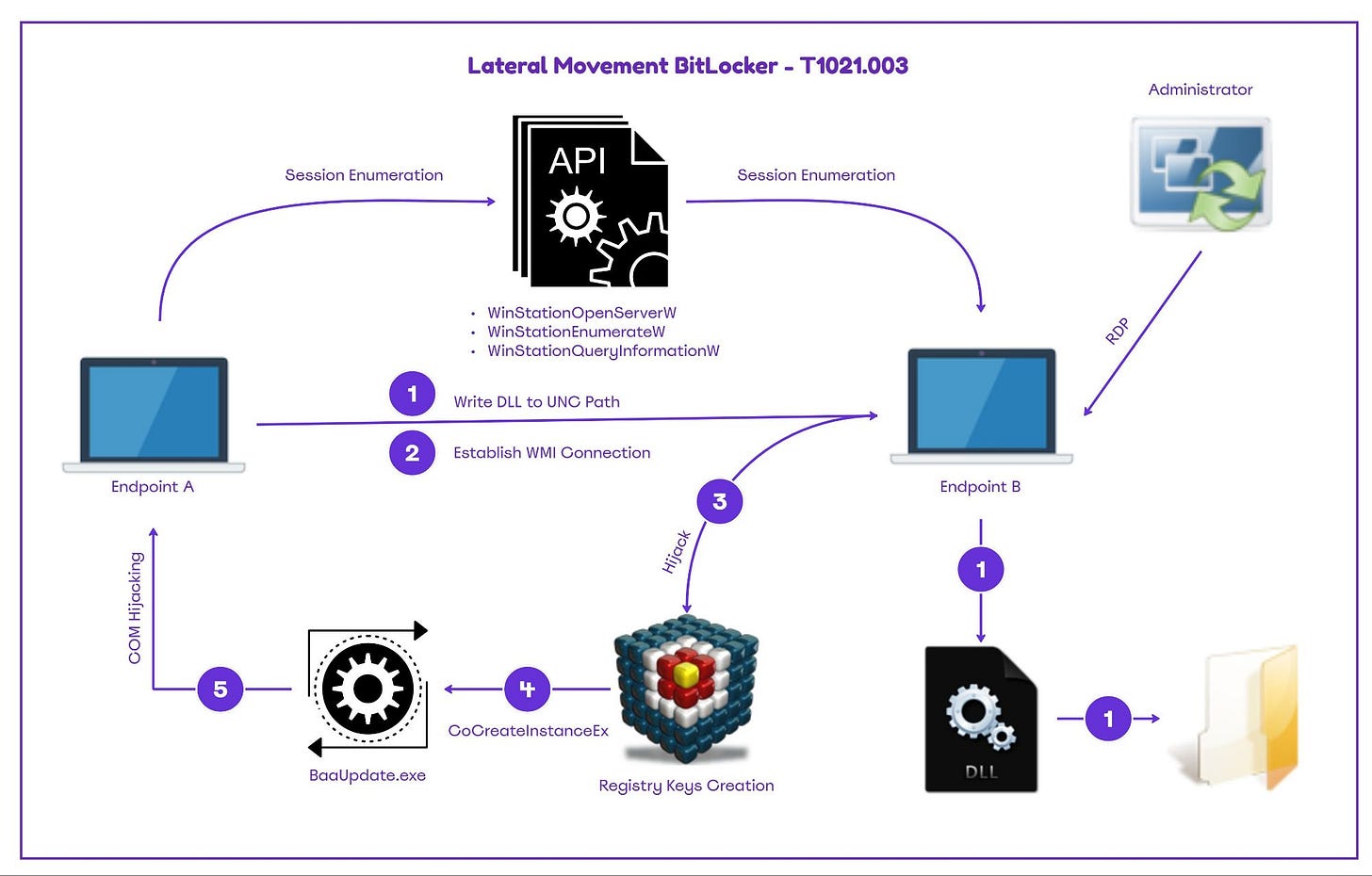
It’s always fun seeing how detection engineers and purple teamers adapt and detect new styles of attack techniques from legitimate security research. In this post, ipurpleteam deconstructs a lateral movement technique dubbed BitlockMove. The BitlockMove technique relies on modifying BitLocker registry keys on a remote machine to drop a DLL as an interactive user.
Fabian Mosch, the researcher who discovered this technique, found undocumented Microsoft API’s in winsta.dll to help enumerate remote sessions. Once the tool finds a vulnerable interactive user sessions, it uses WMI to edit remote registry keys associated with BitLocker and performs a COM hijack to load attacker-controlled code for the lateral movement.
This is possible since one of the BitLocker executables is vulnerable to COM hijacking and tries to load the registry value that was put in by the victim registry in the second part of this attack.
AURORA – Leveraging ETW for Advanced Threat Detection by Swachchhanda Shrawan
EDRs are traditionally kept secret regarding their operations and detection mechanisms. I’ve learned that major EDR companies generally gate their configuration and performance data. Once you pay those same companies lots of money, you’ll get access to a portion of their technology. In this post, Shrawan shows how Nextron’s EDR agent, AURORA, performs threat detection on behalf of their customers. The cool part here is that you can set this whole lab up with their community edition agent, AURORA Lite.
AURORA taps into Windows ETW for telemetry and adds additional fields on top of the logs to help with detection scenarios. The cool part with their deployment strategy is to add Sysmon on top of AURORA for additional logging that ETW doesn’t necessarily support. The part I like the most is the strace-like capabilities to see what the EDR is seeing as you perform threat emulations. Again, something you won’t see a Crowdstrike, Microsoft or SentinelOne doing and lastly, having Sigma rules as the detection language gives a ton of flexibility for detection engineers.
Monitoring Bash readline with eBPF CO-RE & LLM Assistance by Alex Elbaum
This is a fun read for folks who want to go a bit deeper into Linux internals with a constrained problem space: the bash command line. Elbaum explores options for monitoring bash via a flexible eBPF program that can be compiled once and deployed to machines without shipping kernel headers alongside the eBPF program.
eBPF is the leading technology for EDR-style solutions on Linux. Kernel modules can perform this same functionality, but when you hook everything in the Kernel in line, and the complexity of your EDR increases, it can ground airplanes for a few days. Elbaum is transparent in this post such that he ping-ponged between different LLMs to help write these programs. Still, it was cool to see how he leveraged them as a co-pilot to help him research this subject and understand complicated subjects clearly and concisely.
How Message Queues Work by Sid (The Scalable Thread)
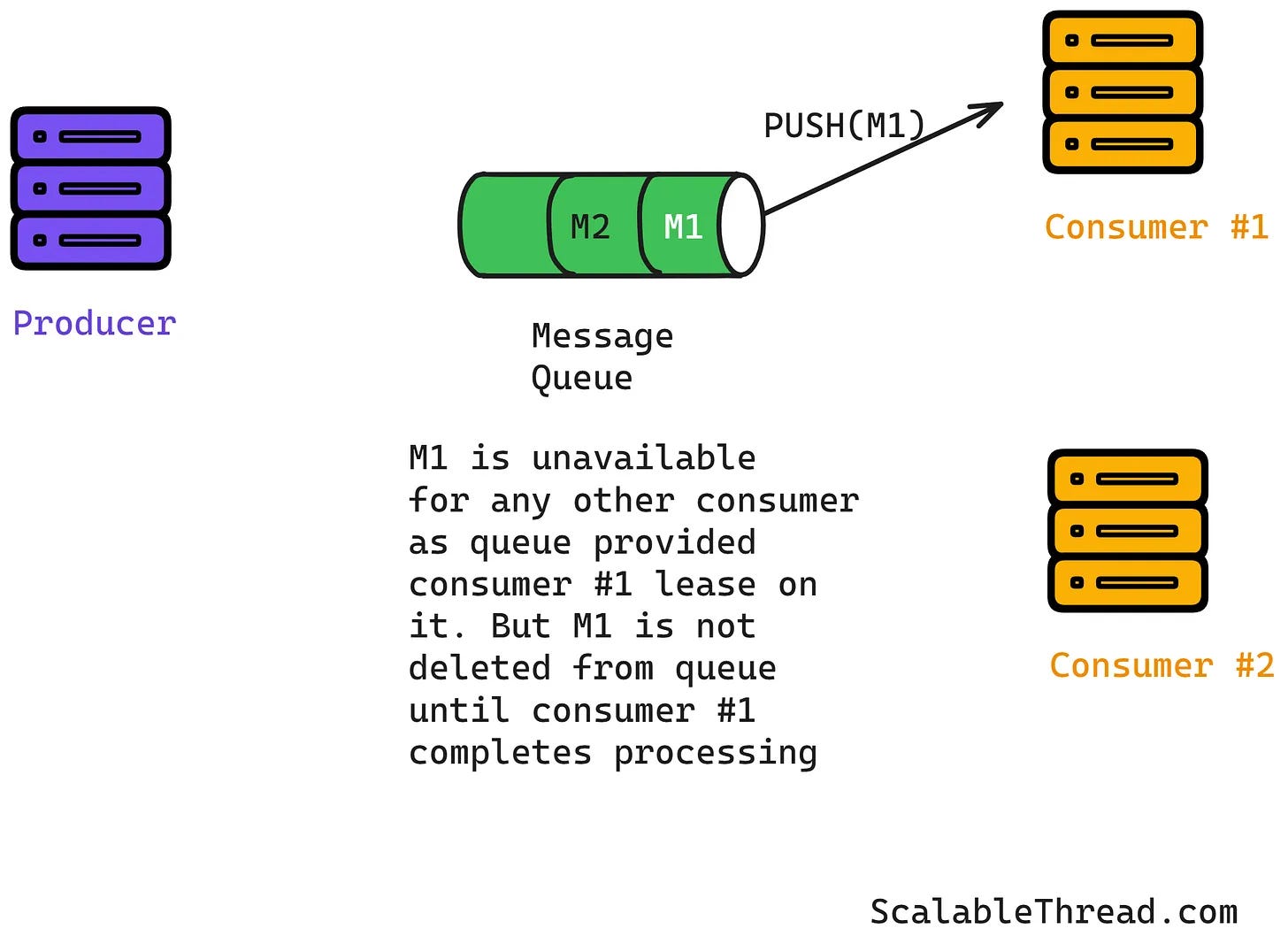
I’ve been perusing and picking out detection engineering-related articles from Sid, and I keep finding so many goodies. In my opinion, it’s so essential for anyone who wants to be effective in our niche field in cybersecurity to understand the engineering architecture principles behind all the systems we use for threat detection. If you read the Gem from last week’s issue about Netflix’s Psycho Pattern, you should have noticed the Kafka queue and watermark architecture on Netflix’s threat detection system. Kafka is a very popular message queue system, and it’s an excellent technology if you want to build a scalable, high-throughput, and fault-tolerant threat detection system.
Once you get the basics of the producer and consumer setup, pay close attention to the Message Lease and Retries section. Since accuracy and timeliness are so important to threat detection systems, you can start to see why using leases and not processing the same message amongst multiple consumers can guarantee consistency and order with detection logs as they flow through this system.
The cool part here is that it’s not always Generate Log → Message Queue → SIEM. The in-between can contain many messaging queues that perform everything from deduplication, normalization, and threat intelligence enrichments.
Trust Me, I’m a Legitimate Process: Verisimilitude and the Art of Hiding by Nasreddine Bencherchali
Nas is back with a banger of a detection post, looking at how the believability of a signal to a defender can hamper analysis or alerting. I admit I had to look up how to pronounce verisimilitude. I’m going to be asking him later if he found this word in one of those apps that expand your English vocabulary, or if this is just the American schooling system failing me.
After 3 practices and rereading his definition, I appreciate it as an apt and pithy description of attacking the visual reasoning of humans and their detections. The basic premise here is that blending in is a massive advantage for threat actors on a victim system, so by zooming out and describing the different types of deception, you can start to understand ways to combat it.
☣️ Threat Landscape
oss-security - Linux kernel: eBPF vulnerabilities
There was some drama on the linux-distro mailing list as a security researcher disclosed high level details on 11 eBPF vulnerabilities. The researcher was supposed to go to the kernel security team first for the responsible disclosure. They may not have understood the process, but they found some significant vulnerabilities that attack a critical subsystem of Linux. Two of them, listed under critical, made my ears prick up: a container escape and a privilege escalation.
Are Scattered Spider and ShinyHunters one group or two? And who did France arrest? by Dissent (Databreaches.net)
I don’t usually link blog posts that interview threat actors because the “interview” is really just allowing criminals to advertise themselves while the interviewer works for a company that wants headlines. But, this is different with the folks at Databreaches. They really care about the analysis of the threat actor, and asking questions where the answers can help researchers and intel professionals understand more about the actor.
So, it looks like ShinyHunters potentially returned to the scene, but the confusing thing here that Databreaches calls out is that they claim ShinyHunters and Scattered Spider “combined.” They get into the technical nuances of why this is kind of a B.S. claim, but it’s nice to see this level of scrutiny on headline-grabbing subjects like this.
U.S. Senate Confirms Sean Cairncross as the National Cyber Director by U.S. Whitehouse
The U.S. finally has a new National Cyber Director after the Senate approved his nomination. To be honest, there’s not much information I could find on Cairncross, other than that he served as the CEO of the U.S. foreign aid agency Millennium Challenge Corporation and that he was a former advisor to Trump in his last term. This website has a bit more history, and it’s clear he’s a lawyer, but I don’t see much of anything on the cyber side.
Perplexity is using stealth, undeclared crawlers to evade website no-crawl directives by Gabriel Corral, Vaibhav Singhal, Reid Tatoris and Brian Mitchel
It’s rare to see respected companies call each other out for poor business practices. So when I saw this blog title, where Cloudflare shot a bold claim across Perplexity’s bow, I knew they had something juicy. Basically, through a series of experiments and complaints from Cloudflare customers, they managed to pinpoint how Perplexity bypasses scraping and bot directives on people’s websites through continual escalation of masquerading their crawlers.
When Privileged Access Falls into the Wrong Hands: Chinese Companies in Microsoft’s MAPP Program by Eugenio Benincasa, Dakota Cary, and Natto Team
I remember first becoming part of Microsoft’s MAPP program years ago. It was an excellent early warning system for my team and my company because we could pre-empt critical Microsoft vulnerabilities by writing rules and finished threat intelligence products for our customers the day Patch Tuesday dropped. The information was juicy, imagine knowing about a CVSS 10.0 vulnerability two weeks before it became public, and you can reverse engineer and write PoCs or rules to catch it!
This is where things get really uncomfortable with Chinese-based companies having access to this same data. In this post, Benincasa and Cary outline the Chinese cybersecurity ecosystem of required-by-law disclosure of vulnerabilities, and how Microsoft has routinely kicked out these companies due to breaking NDA with the MAPP program.
🔗 Open Source
Repo holding the PoC for the BitlockMove technique described above in the State of the Art section.
Alex Elbaum’s eBPF readline project for threat detection of malicious bash commands listed above in the State of the Art section.
My former coworker Matt Maisel released his Cloud-native cyber deception tool after his talk at BSides Charm. It’s a modular framework where you can provide LLMs a pre-loaded prompt to generate scenarios by having them evaluate your environment and adapt the honeypot network to look similar to your cloud infra.
Yet another *GOAT project, this time with a focus on Entra. I would say out of all vulnerable-by-design environments, Entra is probably the most complicated to setup and practice due to the complexity of identity scenarios.