Det. Eng. Weekly #125 - I'm the Miss Rachel of Threat Detection
Uh oh that's a bad rule!
Welcome to Issue #125 of Detection Engineering Weekly!
⏪ Did you miss the previous issues? I'm sure you wouldn't, but JUST in case:
💎 Detection Engineering Gem 💎
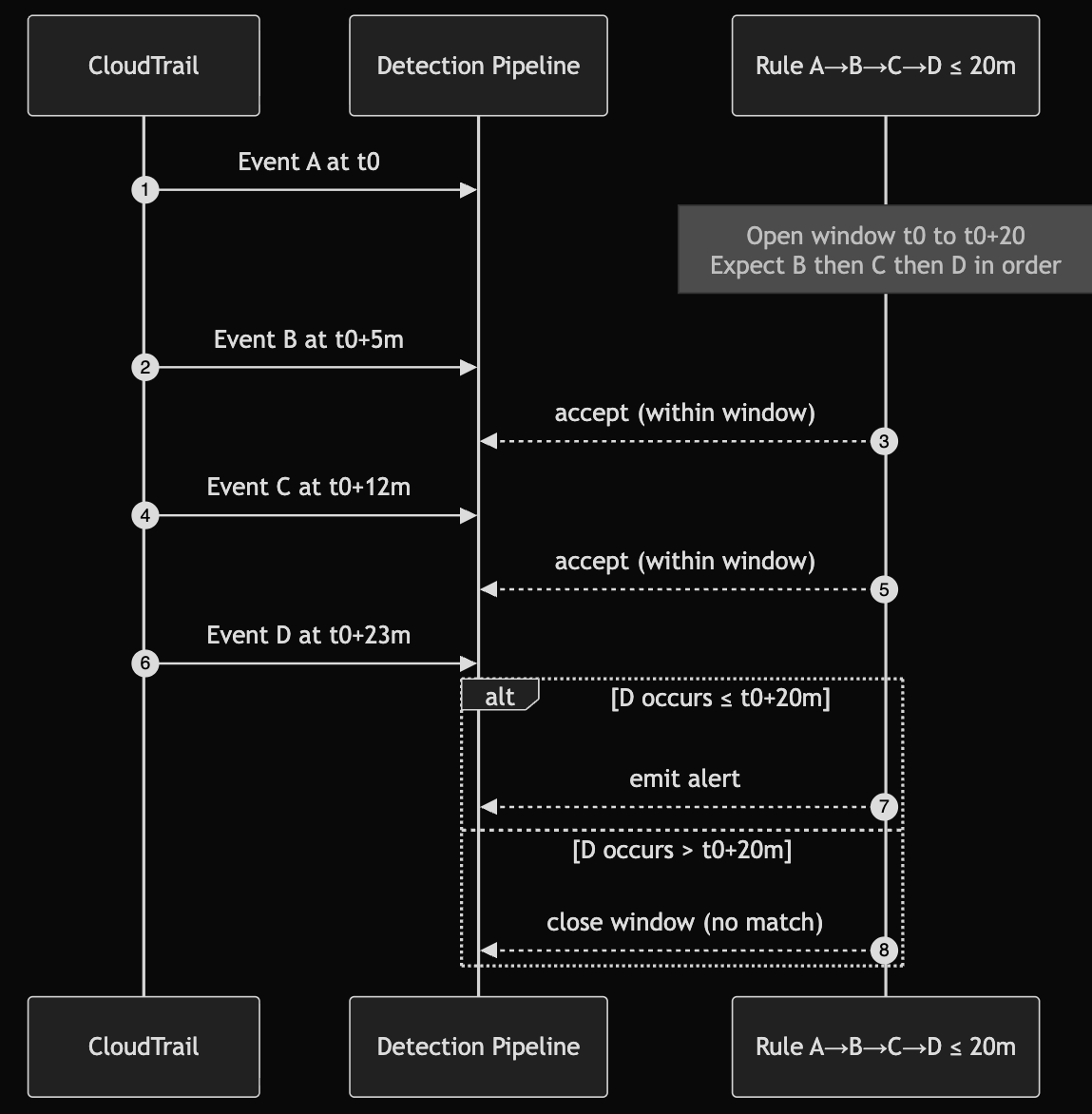
Build a Time-Based Threat Detector with Lambda and Athena by Rich Mogull
My friend Rich wrote an excellent post on building sliding query window detections using AWS services. I saw it on social media, added it to my queue, and lo and behold, he also gave this newsletter a shoutout! I need to return the favor, so please go checkout his Newsletter/Blog Cloud Security Lab a Week.
The cool part about Rich’s blogs is that he breaks posts down into two sections: theory and labs. The theory in this post revolves around sliding window detections and how you can get around the Halting Problem using overlapping windows of log inspection. Essentially, you need to do a batch based lookup of logs to find indicators of maliciousness, but you run the risk of missing a window of logs if you do sequential windows. Here’s a visual from his blog:
This reduces the risk of missing critical logs you get when doing sequential windowing. I took Rich’s windowing visual and tried to show it using Mermaid (and so it can fit inside the newsletter!)
Notice here that the Windowing period is 20 minutes. Each CloudTrail event flows into the pipeline, and A, B and C all arrive in 12 minutes or less. Event D, however, is at 23 minutes, which means it’s outside the window and the alert is scrapped. The alt box shows what would happen if it arrived in 20 minutes or left (alert).
The Lab section uses a CloudFormation stack to boot up all of the necessary infrastructure, and you can see, feel and click on the infrastructure, logs and alerts to see how it all works under the hood. He also has a video walkthrough if folks prefer a more visual walkthrough.
🔬 State of the Art
From Telemetry to Signals: Designing Detections with an Audience in Mind by Nasreddine Bencherchali
Nas is SO back.
And by back, I mean cranking out highly relevant posts discussing super insightful topics, so make sure to go check out and subscribe to his Medium. In this post, he explains the nuances behind the customer archetype of a detection rule. Security Operations departments and teams all look different. Some have a massive scale with humans, technology and several departments looking at various parts of an attack chain, while others have 4-5 Detection & Response engineers responding to everything. Nas calls this “Schrödinger’s Detection”.
With this in mind, does it make sense to write one rule that can fit the needs for the following “archetypes”?
Incident Responder
SOC Analyst
D&R Engineer
Software Teams owning the Detection and SIEM Infrastructure
Nas outlines the needs of each of these archetypes and the incentive structure behind their security work. For example, if you ship a rule that casts a wide net and looks for an IP address, a small team of 5 D&R Engineers or a SOC will yell at you. But this could be super useful for an Incident Responder. I’ve hit this concept hard with my detection teams to make sure that we think about the consumer of our detections first, and then we can think about the usefulness of what we ship into production.
This is an apt quote from the blog on setting expectations:
This is why setting expectations is technically not optional, it’s the difference between a detection being understood and valued versus misunderstood and scrapped.
DFIR Artifact: PowerShell Transcripts by Eric Capuano
PowerShell Transcripts are like a “flight recorder” for PowerShell, as Eric puts it. Since PowerShell is so heavily used in threat actor and system administrator operations, its logging their execution details and associated metadata is essential for DFIR engagements.
Eric walks readers through the configuration and deployment options for transcripts and shows several examples of what the transcripts look like and how to parse them. Lastly, he adds my favorite part of any detection blog: detection opportunities!
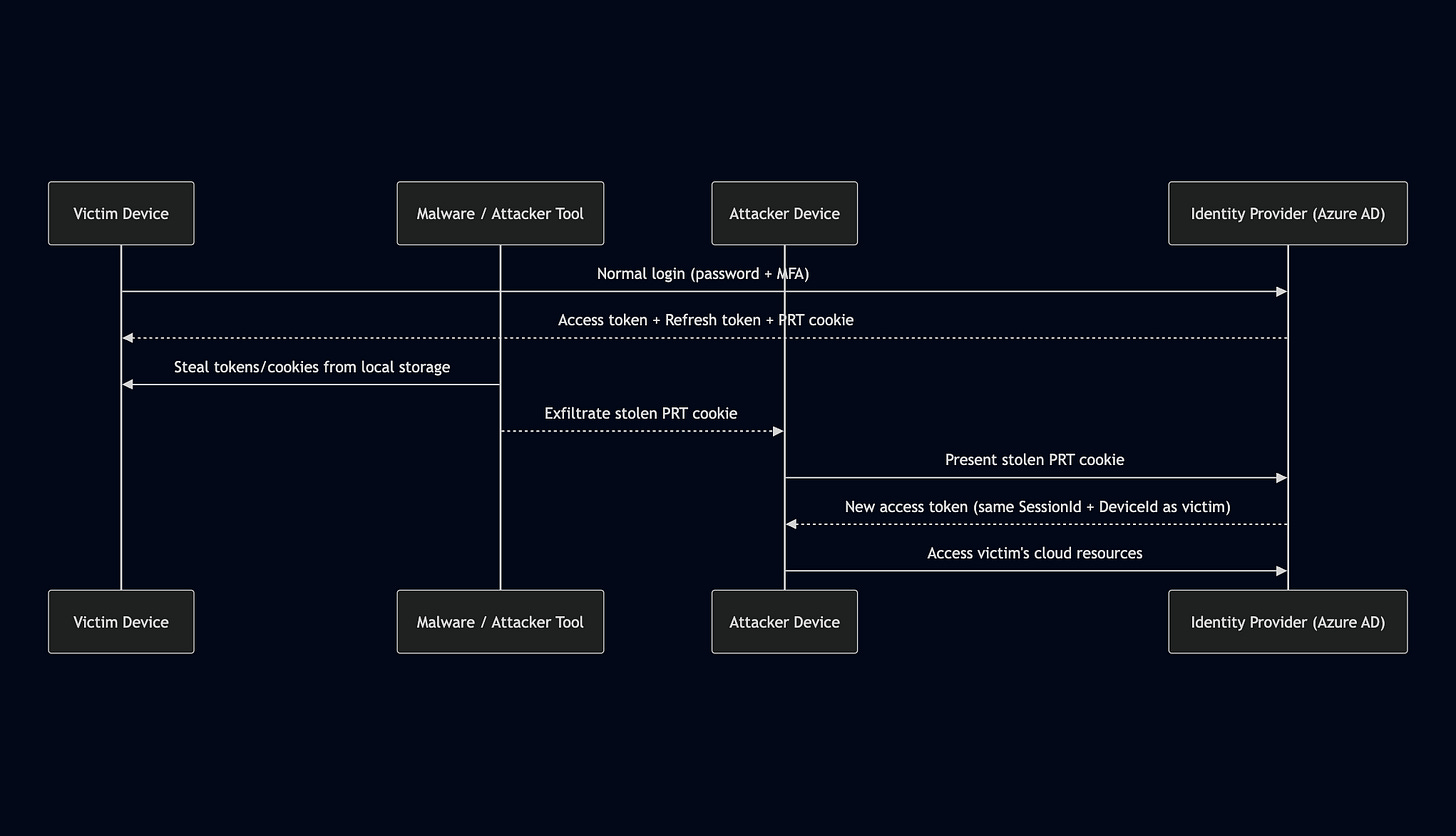
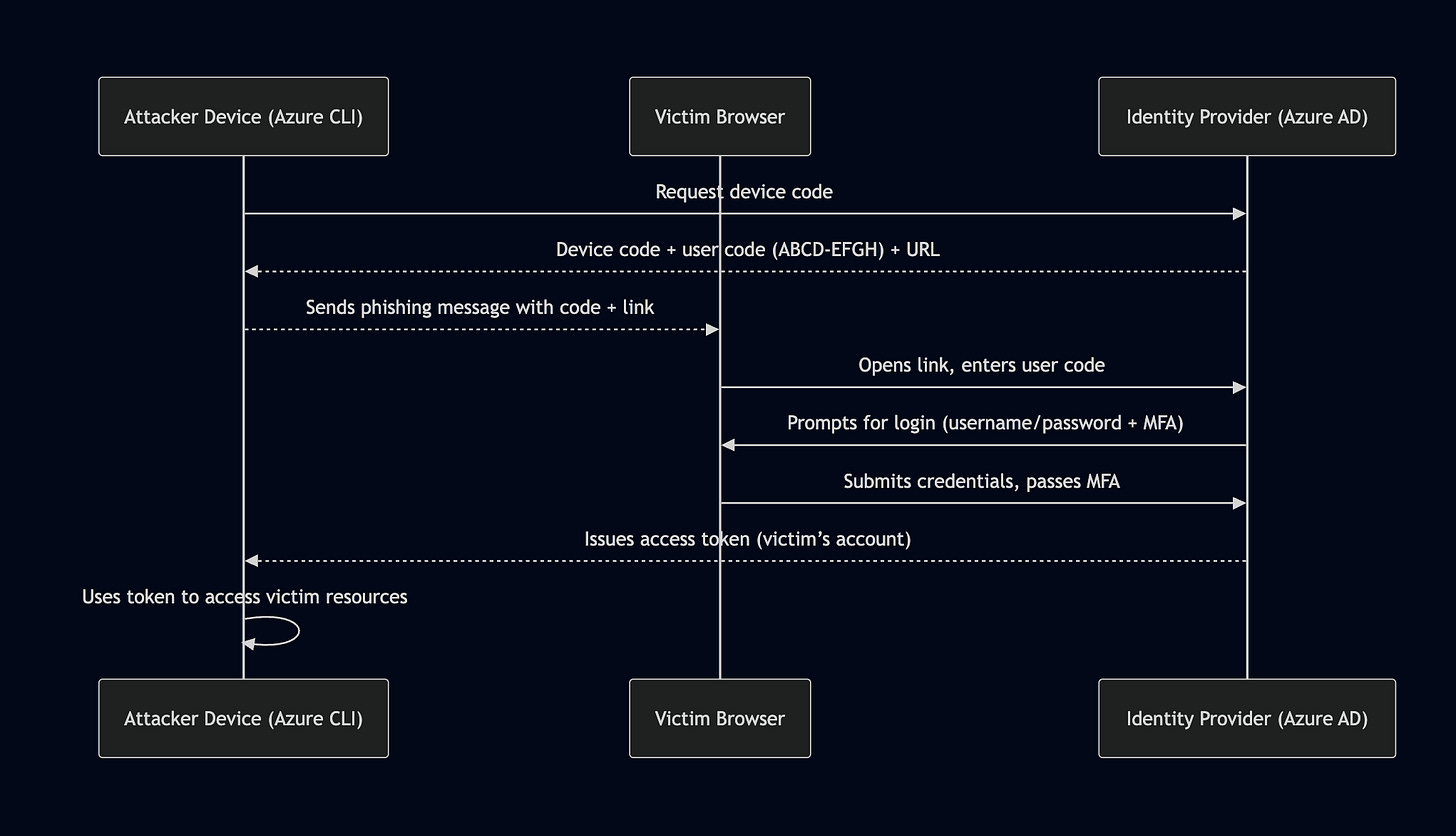
The Hidden Gaps in Microsoft’s New Linkable Token Identifier by Mehmet Ergene
Mehmet’s latest update on new Microsoft Threat Detection products sheds some light on their latest feature, linkable token identifiers. The basic idea behind the identifiers is that Entra Security Logging has more metadata around particular actions within the SignIn workflow, and it can help link together events using the same session ID. This is useful for detecting and shutting down Adversary-in-the-Middle (AitM) phishing attacks.
According to Mehmet, this helps with AITM attacks, but leaves out other, more recent phishing-style attacks against Entra/Azure. He goes explicitly into two types of phishing TTPs: device-code phishing and Token Stealing. I had ChatGPT build two Mermaid diagrams to visualize both, but make sure to go read the “why” and detection opportunities from his blog.
FortMajeure: Authentication Bypass in FortiWeb (CVE-2025-52970) by BigShaq
I love vulnerability write-ups that use an exploit that attacks a cryptographic implementation to nullify a cryptographic primitive. BigShaq was poking holes at FortiWeb and found an auth bypass where attackers craft a number between 2 and 9 (lol) on an attacker-controlled parameter and force a cryptographic key to be all 0s. Since the key is all 0s, they were able to sign an HMAC message that matches the key (all 0s), and get a FortiWeb webshell.
How XProtect’s detection rules have changed 2019-25 by Howard Oakley
XProtect is Apple’s defense-in-depth technology that remediates and blocks known malware after it executes on a macOS device. It comprises of YARA rules that act as generic signatures for common malware patterns, so when it detects something on the device, it’ll block execution and move it to the Trash. Apple stores these rules in a single text file, and Oakley has been tracking Apple Security Engineers’ maintenance of this file for several years.*
The number of YARA rules has increased to nearly 400 in the latest release, and according to Oakley, it appears that they haven’t removed any rules affecting older versions of macOS. This is especially interesting when you consider Apple’s switch to its Silicon processors, which means not every device can run malware developed years ago. This ballooning of rules has affected how long it takes Apple’s GateKeeper to run, so hopefully they trim the size of this ruleset, or malware will probably just beat GateKeeper in doing its objective before the YARA rule runs.
☣️ Threat Landscape
Datadog threat roundup: Top insights for Q2 2025 by Greg Foss, Andy Giron and Matt Muir
~ Note, I work at Datadog, and Greg/Andy/Matt are all my colleagues! ~
The Security Research and Intelligence team at Datadog just published our Q2 threat roundup. We found lots of interesting attacks this quarter targeting the open source supply chain, containerized workloads and cloud environments. The highlight of this quarter was uncovering new TTPs from Mimo, who started building out their rolodex of CMS vulnerabilities and targets to deploy their malware.
Remote unauthenticated command injection by Fortinet PSIRT
This is a different CVE than the FortMajeure CVE listed above in State of the Art. CVE-2025-25256 affects Fortinet’s FortiSIEM product, which makes this even funnier because it attacks a security product that is supposed to detect attacks just like this one. Fortinet PSIRT says there are already practical exploits in the wild for this, so put your SIEM behind a gateway and don’t expose it to the Internet!
LazarOps: APT Tactics Targeting the Developers Supply Chain [PART 1] by SecurityJoes
I’ve posted several articles focusing on DPRK-Nexus threat actors compromising developers and the software supply chain. I’ve never seen an article on this subject from an Incident Response team that helped remediate an incident for a victim. This looks like a typical Contagious Interview attack chain, where the developer was contacted by a fake recruiter and tasked to solve a coding test in a malicious GitHub repository. The updated TTPs I’ve seen here include iterating through a list of 1000 potential domains in a pastebin file if the initial C2 communication fails.
How attackers are using Active Directory Federation Services to phish with legit office.com links by Luke Jennings
This is an excellent follow-up post on phishing techniques to Mehmet’s post above, so make sure to read that one first. During his phishing kit research, Jennings found a peculiar malvertising-style phishing page for Microsoft accounts.
Attackers found a clever open-redirect in office.com, not due to a vulnerability or open parameter, but rather due to how Office performs redirects to ADFS tenants for authentication. By creating an attacker-controlled ADFS tenant, you can tell Office to redirect to your Azure infrastructure, where you control the chain of redirects. This helps attackers make victims believe it’s a legitimate URL since it’s from the Office domain.
From Bing Search to Ransomware: Bumblebee and AdaptixC2 Deliver Akira by The DFIR Report
Excellent and concise DFIR Report write-up on an SEO poisoning attack that led to Akira ransomware. The threat actor targeted victims searching for OpManager and presented a fake website that packaged the legitimate software with Bumblebee. They installed AdaptixC2 next and began moving laterally throughout the network. Once they hit the primary domain controller, they exfiltrated sensitive files and started encrypting the network with Akira.
🔗 Open Source
IDA Pro plugin that helps generates cross-references (XRefs) that IDA missed. It particularly focuses on modern compiled languages like Rust/Go/C++ and binaries with some advanced obfuscation techniques. It does note it’s designed to be used alongside Mandiant’s XRefer plugin.
0xJs/BYOVD_read_write_primitive
This is a neat PoC repository of several BYOVD techniques. The README contains excellent walkthroughs of each method and the -h output of the binaries with corresponding arguments.
arosenmund/defcon33_silence_kill_edr
Open-source release of a DEFCON 33 training dubbed “Putting EDRs in Their Place”. It’s a collection of techniques designed to bypass and kill EDRs once you land on a victim system that has the security tool in place. They have a bunch of setup tools, an emulated EDR, VMs, and an explanation of the techniques in their README.
Post-exploitation framework with your typical C2 operations, but with a front-end that looks similar to Cobalt Strike. You can build payloads cross-platform, use it as a teamserver to coordinate operations and write extensions to take advantage of it’s flexibility.



These visuals are 🔥🔥