Det. Eng. Weekly #115 - I want my threat actors named like my ice cream
Chocolate Chip, Jamoca and Reese's Blizzard
Welcome to Issue #115 of Detection Engineering Weekly!
OK, so I made a mistake. I do this all the time, and I wish I had an editor or an AI to check my work here.
In the last issue, I linked a Detection Engineering Weekly company page on LinkedIn. I asked you all to join and discuss topics with me. But you can’t do that on a company page because discussions can only occur in groups.
So, can you all follow/like the newsletter group? https://www.linkedin.com/groups/13266114/
I’ll be reading your posts and discussions to potentially link in the newsletter, and will be posting more stories so you can get them directly to your LinkedIn notifications as I find them.
Thanks fam’
⏪ Did you miss the previous issues? I'm sure you wouldn't, but JUST in case:
💎 Detection Engineering Gem 💎
Detecting Malicious Security Product Bypass Techniques by Andrew Schwartz, Matt Anderson, Tyler Bohlmann, Anton Ovrutsky and Greg Ake
Huntress researchers perform a deep technical analysis on defendnot, which I linked in Issue 113. Their analysis is of course way deeper than my meme posting, but I love the concise framing of the “Malicious AV Product” technique that Huntress coined here. Through the abuse of legitimate processes registering themselves as a Fake AV product, attackers can abuse the privileges when registering an AV to turn off other legitimate AVs.
The impressive part with defendnot is that the researcher who wrote it spent a ton of time reverse engineering Windows Security Center APIs to build it from scratch. These APIs are mostly undocumented and require an NDA for companies to get access to how-to documentation on their use.
According to the Huntress researchers, you can’t just inject any Windows process into the WSC functionality. There are several checks implemented by Windows to make sure the process is known by the WSC through a series of validation checks.
The cool part about this blog is that every step listed above has detection opportunities. Some are lower fidelity, like monitoring new process creation, but when combined with other parts of the attack diagram, can likely detect defendnot. For example, the binary creates a configuration file on disk before it creates a DLL and injects it inside a victim process. This is a great spot to write some rules since it’s a necessary condition.
🔬 State of the Art
5 Lessons Learned as Incident Commander of the Biggest Security Incident of My Career by Ryan G. Cox
As someone who’s had their fair share of security incidents, it’s really nice to see someone highlight the less technical but just as important role in incident response: the incident commander. In this post, Cox breaks down 5 lessons learned during a recent major security incident he responded to. This is a lesson in leadership more than it is a security deep dive, but these “soft skills” pay in dividends once you employ them.
For example, do you think you know about every system, every log and every service at your company? Probably not, but you may be responding to a threat actor accessing one of these systems. So, building out relationships out of the security team, such as engineering or IT, accelerates your containment and ability to call in the right people to help.
My favorite section on post-mortems is the last section of the blog, maybe intentionally :). An incident should ALWAYS result in after action items, and in our world, that hopefully leads to new controls, better logs and new detections.
Detecting Vulnerable Drivers (a.k.a. LOLDrivers) the Right Way Using Microsoft Defender for Endpoint by Mehmet Ergene
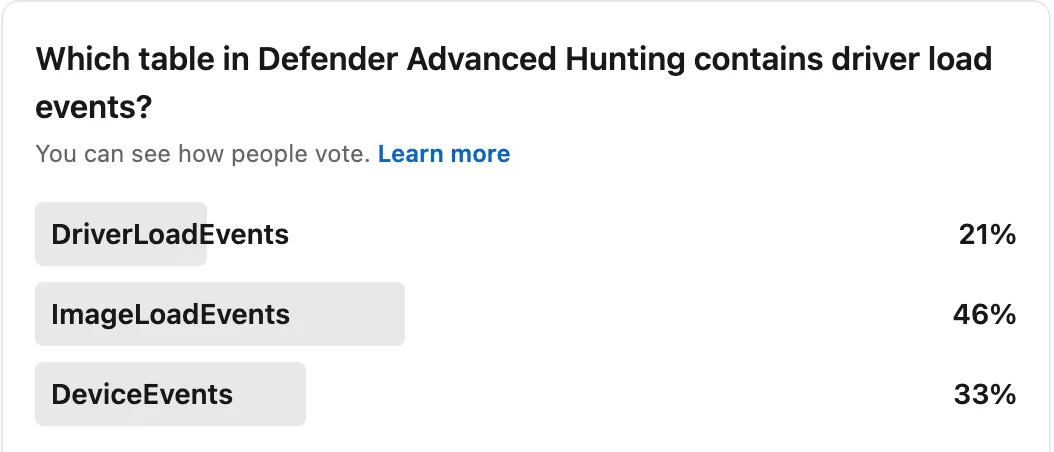
I appreciate the premise of this post from Mehmet; his content is driven by a poll he took on a specific detection opportunity. Mehmet asked readers and followers a specific example around a detection idea..
…and then broke down each response. I felt like I was in college all over again and I rose my hand for the wrong answer :3.
In all seriousness, I think this is a cool way to teach people a methodology behind answering questions around detection opportunities rather than the specific question itself. Basically, over 2/3 of responders got this question wrong and it looks like they could’ve found out if they just Googled it.
DeviceEvents is a table in MDE that shows events loaded from drivers with a .sys extension. You can use those load events as a way to find potentially malicious loading of loldrivers. He includes the detection at the end of the post, so how much more can we ask for?
Ghosts in the Endpoint: How Attackers Evade Modern EDR Solutions by Matt Fuchs
This blog serves as a compendium on EDR bypass techniques. Fuchs lists five common techniques and after spending two years studying Windows security and linking them here on the newsletter, I felt pretty good knowing what they were! Each section contains a description of the bypass technique, several real-world examples of threat actors leveraging those techniques, and how EDRs typically defeind against the technique.
My favorite section is towards the end, “BYOVD - Bring your Own Vulnerable Driver.” These are attack classes that leverage signed and trusted drivers, which run in Kernel mode, to evade or straight-up kill the EDR. As Fuchs puts it, it’s using the Windows security model against itself in the sense that it abuses a trusted cryptographic signature to allow-list the vulnerable driver.
I’ll point back to this Microsoft learning article if you want to go a bit deeper on how Microsoft implements protections against all of these techniques.
CloudTrail Logging Evasion: Where Policy Size Matters by Abian Morina
Ok this is a hilarious vulnerability, and it’s relevant for detection engineers because it’s a fun way to evade logging for threat detection. Morina and Permiso research figured out that you can mess with the IAM policy size limit using whitespace padding. Although AWS specifies a policy character limit, it explicitly states that whitespace is not counted as part of that limit. So, by exceeding the policy limit, CloudTrail says it can’t display the logs due to the character limit but still stores the malicious IAM policy.
☣️ Threat Landscape
CrowdStrike and Microsoft Unite to Harmonize Cyber Threat Attribution by Adam Meyers
It finally happened. A Rosetta Stone for threat actor names. It’s never been tried before, but this time I think we can do it /s. In all honesty, I’m hopeful, but I have skepticism about blogs like this. It’s like the Cybersecurity Pledge from CISA; people signed it, but did they actually do anything? They included an Excel file with all their mappings, so that’s nice!
Again, excited to see what they actually do with this translation layer.
Tracking AyySSHush: a Newly Discovered ASUS Router Botnet Campaign by Himaja Motheram
This is a neat Internet-wide study on the AyySSHush botnet. First uncovered by GreyNoise, AySSHush targets ASUS routers via a 2-step exploit chain: login via default credentials or weak credentials, and an authenticated command injection vulnerability. Once inside, it opens SSH on a high port, sets a public key, and persists via authorized_keys. Since the authorized_keys file is in a router-wide configuration directory, it persists across firmware updates.
Re: [GIT PULL] hardening fixes for v6.16-rc1 - Linus Torvalds response to some "strange" Git commits to the Linux Kernel by Linux Torvalds
Ok this is not a blog post, but a thread from the lore.kernel.org legendary mail list. Kees Cook, a long-time committer to the Linux Kernel, committed a bunch of code and opened a pull request to merge into the Linux Kernel. From what I can interpret, there were some honest mistakes made around some tooling updating commit history dozens of commits back instead of the intended commit.
WTF, Kees?
You seem to have actively maliciously modified your tree completely.
There are completely crazy commits in there that are entirely fake.
Linus goes off on Kees, making some accusations that he is trying to introduce malicious code to the main branch of the Linux kernel. He asks another administrator, Konstantin Ryabitsev, to disable his account until the situation clears up. It appears that they did, but in Linus’s fashion, he was brazen in his feedback.
Kernel security is a critical problem to solve, considering the downstream effects it could have on the “sanctity” of the Linux kernel. You don’t want another xzutils.
Mysterious leaker GangExposed outs Conti kingpins in massive ransomware data dump by Jessica Lyons
A vigilante Batman-like hacker, GangExposed, has been on a tear outing and doxxing alleged members of the former Conti and TrickBot malware gangs. According to Lyons and via direct Signal chats, GangExposed’s motives seem righteous. He did not want to claim the FBI’s 10 million dollar bounty, so he started publishing names, business details, photos and even the kind of cars some of these gang members drive. He doxxed Stern, the leader of Conti, and German Police went public with Stern’s name a few days after his post.
BPFDoor Part 2 - The Present by haxrob
BPFDoor is a Linux BPF-style rootkit that has changed the way Linux rootkits are viewed for malware research. Instead of a kernel module or a user-land rootkit leveraging LD_PRELOAD, BPFDoor uses Linux’s Berkeley Packet Filter functionality to essentially tap into raw sockets and look for specific traffic to provide remote access.
Since BPFDoor has been attributed to Chinese-nexus threat actors, you can imagine it gets updated to help prevent detection. Haxrob dives into the latest features found on new samples and provides their technical analysis of these changes, alongside detection opportunities (and YARA rules!) to hunt for new infections.
🔗 Open Source
Google released their MCP server for their security operations and threat intelligence products. You run their servers on whatever infrastructure you have and then use an MCP client (via Claude, for example) to issue queries and the server will translate them to the Google API backends.
microsoft/AI-Red-Teaming-Playground-Labs
This is a 12-part “playground” for practicing red-team attacks against LLM systems. You can refer to the table for the various CTF-style challenges, ranging from secret extraction to bypassing guardrails.
Post-exploitation Red Team Toolkit for Linux Systems. It has 14 separate techniques mostly focused on evasion, persistence and some privilege escalation. They have a separate repository with ASCII Cinema demos here.
A large database with over 1600 regular expressions and secret formats for secret scanning. Has native tooling to convert to tools like TruffleHog and gitleaks.
cloudflare/workers-oauth-provider
Native OAuth Provider for Cloudflare using their workers product. The crazy part of this project is here in the README:
This library (including the schema documentation) was largely written with the help of Claude, the AI model by Anthropic. Claude's output was thoroughly reviewed by Cloudflare engineers with careful attention paid to security and compliance with standards. Many improvements were made on the initial output, mostly again by prompting Claude (and reviewing the results). Check out the commit history to see how Claude was prompted and what code it produced.