Det. Eng. Weekly #112 - ]ffcvbhvvji90
My daughter wrote that title and I think it'd make a good name for Elon's next kid
Welcome to Issue #112 of Detection Engineering Weekly!
📣 New Detection Engineering focused conference: Datadog Detect
I am super excited to announce that Datadog’s Security Research team (where I work, full disclosure) is hosting a Detection Engineering conference! It’s free, fully-online and has about 2 hours of content lined up from amazing folks from places like Haider Dost (Snowflake), Rich Mogull (Firemon), Wade Wells, Christine Le (Datadog) and Julie Sparks (Datadog). Every single one of these names have been featured in this newsletter, so even cooler!
It’s on May 29 at 12PM ET. I’m giving the opening remarks/keynote, and I’d love to see you all there. There’s Q&A so you can absolutely troll me.
Click here to register 👉 http://bit.ly/datadog-detect
~ Note ~ This is my employer, and with this current iteration, we do require a form sign up. Feel free to sign up / unsub, but you might have to wait until after the con.
⏪ Did you miss the previous issues? I'm sure you wouldn't, but JUST in case:
💎 Detection Engineering Gem 💎
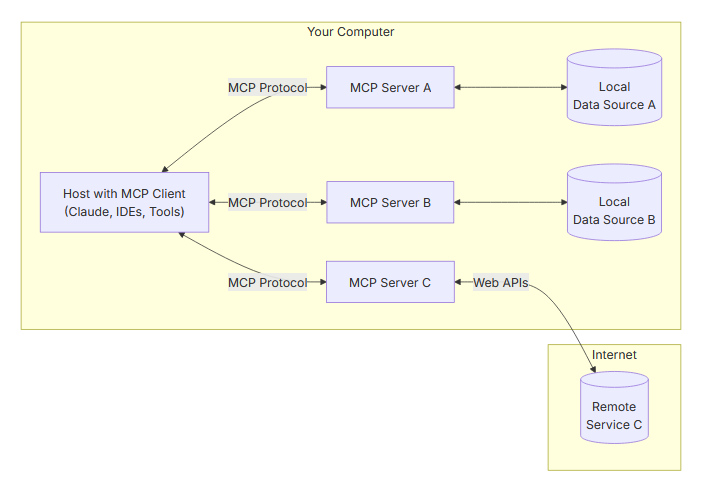
Building Own MCP - Augmented LLM for Threat Hunting by Eito Tamura
This is the most comprehensive threat model I've seen for MCP servers since they entered the zeitgeist of developers and security. If you aren't familiar with MCP servers, LLMs, or AI in general, Tamura provides an excellent introduction at the beginning of the post and increases technical details. There are a ton of risky attack surfaces between client and server, and it's wild to me that an MCP can answer your questions that may result in arbitrary code execution.
The blog doesn't stop there, though! After reviewing the MCP threat model, Tamura helps readers set up an MCP lab environment for threat hunting and log analysis. Part 2 of the blog is about setting up the architecture, which includes an ELK stack plus its MCP server, a local Claude with an MCP client, and a vibe-coded custom MCP server to contact threat intelligence sources.
Part 3 is MCP's threat emulation and testing for hunting and analysis. I'm surprised at how well it did with (minimal) investment from Tamura. You see a ton of startups doing "AI SOC" analysts for this specific scenario, and although they look prettier than Tamura's setup, the outputs generally look the same. He went over three scenarios: investigating mimikatz telemetry, a malicious file being downloaded, and some log analysis.
🔬 State of the Art
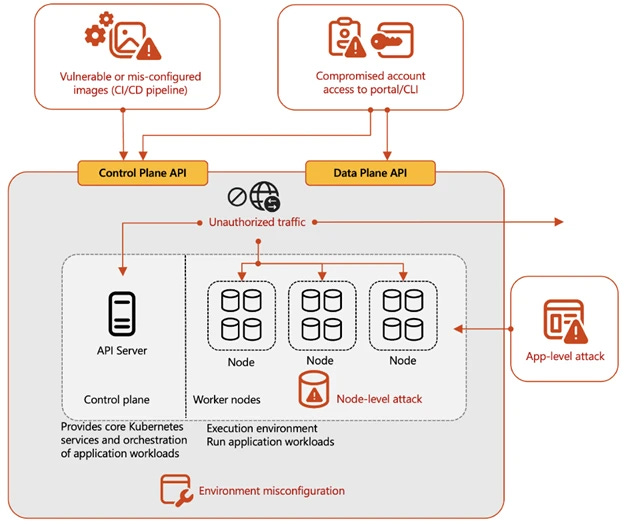
Understanding the threat landscape for Kubernetes and containerized assets by Microsoft Threat Intelligence
Microsoft released a relevant and timely threat intelligence survey on real-world attacks affecting Kubernetes environments. The study did not limit itself to Kubernetes but to everything from individual containers, their registries, and their workloads. Think of the attack surface for Kubernetes as anything that runs an application or server, down to the code running inside a container.
Unfortunately, they include only one attack, AzureChecker, that they observed exploiting Kubernetes. Most of the infection chain includes brute forcing publicly facing Kubernetes clusters and workloads, so it's not too sexy but still relevant. And in Microsoft fashion, the blog contains hardening guidance and then blasts the reader with all of the security tools they sell that their customers can use to harden.
Detecting Anomalous Parent-Child Process Chains: A Practical Guide for Endpoint Security by Paritosh Bhatt
LOLBAS techniques make detecting and investigating harder for defenders. It's like a burglar breaking into rooms in your building using a toolbox they stole from your utility closet. This means they can blend in more with your telemetry because their binaries and tools are part of your environment, making it harder to separate the benign and malicious traffic.
This blog post by Bhatt dives into LOLBAS detection via Parent-Child process relationships. If you are unfamiliar with process trees, Bhatt provides a visually intuitive background on why operating systems leverage them for normal operations. The same technique that threat actors exploit (LOLBAS) is the exact detection opportunity you can use to find abuse. Bhatt documents several examples of malicious parent and process-child relationships and detection opportunities using sysmon, SIEM, and EDR solutions.
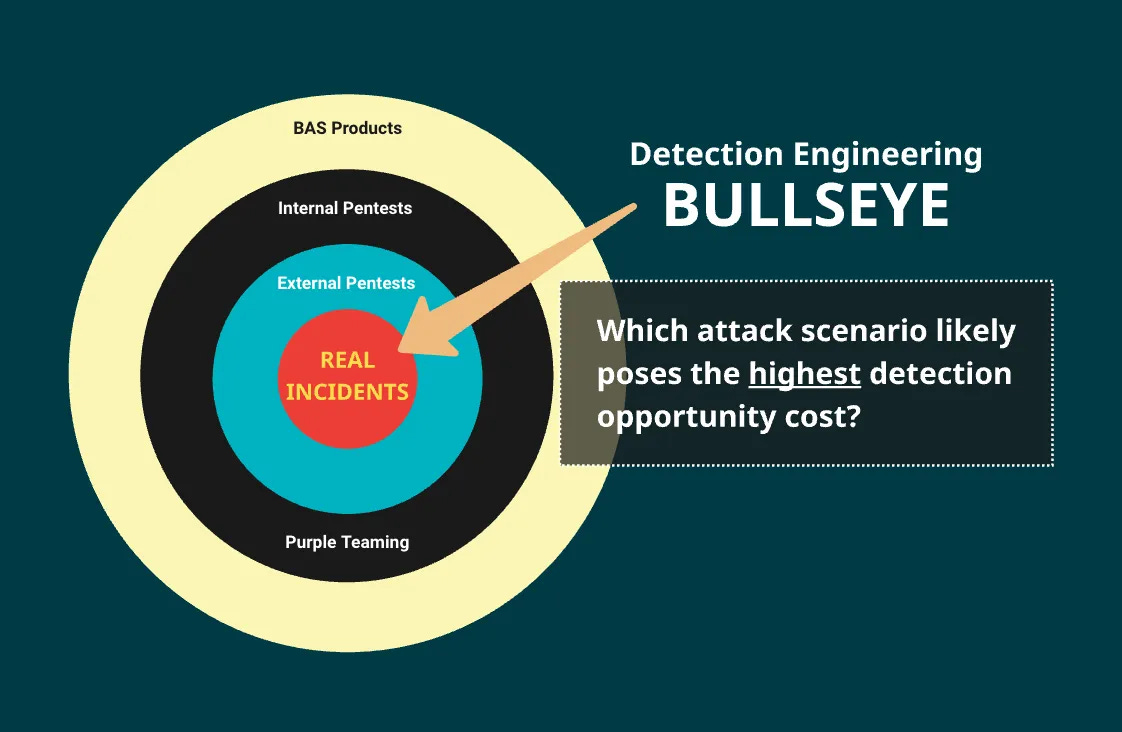
The Detection Opportunity Cost by Alex Teixeira
The Detection Backlog is an absolute necessity for threat detection teams. Without organizing your detection ideas, you won't be able to prioritize. If you can't prioritize, you lose the history of why you ideated the detection in the first place, or you work on things that may not matter because you never went through the prioritization exercise. Alex assigns a weight to the latter, the "Detection Opportunity Cost."
I appreciate Alex taking ideas from other fields, especially business, and applying them to security. The basic premise behind opportunity cost involves looking at a series of decision points and balancing the cost of making the decision now versus at some later event. A good example of this is in physical supply chain economics. When you anticipate increased inventory costs due to a pandemic or tariffs, you want to invest time in the present to build or find additional suppliers and incur the cost now versus when these externalities kick in, and the price is way higher.
So, what's the opportunity cost of a detection idea that is irrelevant to your environment? You pay a high price to create it; the benefit is minimal since an incident is unlikely. Learning from existing incidents and threat intelligence related to your environment are excellent ways to incur the cost before it becomes more expensive later.
Top Tier Target | What It Takes to Defend a Cybersecurity Company from Today’s Adversaries by Tom Hegel, Aleksandar Milenkoski, and Jim Walter
This unique blog post from SentinelOne focuses on how threat actors target them versus their customers. This topic is one of the sobering realities of working at a security product vendor, and it should be something you think about as you purchase and use your security vendors. The researchers outlined three separate scenarios they've faced: fake IT applicants from North Korea, criminals targeting and reverse engineering their EDR technology, and ransomware operators and nation-states trying to gain initial access to their firm.
I appreciate the transparency in blogs like this. Typically, security vendors try not to tip their hands to threat actors on their defensive strategy, as it can help them adjust their TTPs. Transparency leads to trust, and it's a value that I appreciate dearly, and I know the security appreciates it as well.
The end of the blog contains some excellent threat modeling and defensive strategies for companies and teams. The supply-chain element is the most harrowing for me; these types of actors target not just your vendors but also your resellers and suppliers.
☣️ Threat Landscape
Rise of Oriental Gudgeon by URLScan Threat Research Team
I am so excited to see URLScan start making posts with its very own research team! I’ve used this product for years, and it has a community and researcher account for doing your own research. The problem I’ve always had with phishing research (and even in my own publications) is linking to the sites from a forensics perspective, so seeing the URLScan team link public scans helps readers understand more about a particular campaign.
In this post, the research team uncovered a massive phishing cluster targeting Japanese victims. Check out how they broke down the phishing kit victim flow and the detection opportunities. This is so unique to kit research and hunting that it does require a bit more studying than a pure Sigma rule, but once you start finding hunting artifacts for kits, you can make all kinds of searches in platforms like URLScan to detect new ones.
House Passes Latta's ROUTERS Act and NTIA Reauthorization Act by Representative Bob Latta & Ashley Juhn
Representative Latta made a press release to announce the passing of two acts: the ROUTERs Act and the National Telecommunications Information Administration (NTIA) Reauthorization Act. Both of these acts seem to address the Volt & Salt typhoon attacks against telecommunications companies, specifically helping consumers of these companies to protect the routers and modems managed by the telcos. The Bill directs the Secretary of Commerce to perform a national security risk analysis of these consumer devices within 1 year.
A New Kali Linux Archive Signing Key by Kali Linux
It looks like Kali Linux lost access to the signing key in their GitHub repository, which contained their archive signing key. This event marks the second time in seven years they have had to reroll the key. According to their Q&A section, it was not a compromise, which is a good thing, but it looks like users who don't want to pull the latest Kali image have some work to do to update the key.
Messaging app seen in use by Mike Waltz suspends service after hackers claim breach by Kevin Collier and Ben Goggin
The biggest OPSEC news in the mainstream media surrounds Signal and now a secondary “Signal-like” app called Telemessage. TL;dr, a photo of Mike Walz using Telemessage at a meeting leaked to the Internet, and close to 1 week later, suffered a data breach. Telemessage executives shut the app down completely, and according to Collier and Goggin, a credible threat actor stole the data and is sifting through their loot as we speak.
Defending Against UNC3944: Cybercrime Hardening Guidance from the Frontlines by Mandiant Incident Response
The Mandiant team published some up-to-date control guidance for battling Scattered Spider. Unlike anything I’ve seen in other ransomware or criminal actors, the interesting control recommendation is the social engineering angle. I imagine there’s a ton of pain with IT Helpdesk workflows that require out-of-band communications, photo ID verification, and challenge/response questions.
🔗 Open Source
PrimeEncryptor by dagowda
Dynamic Shellcode Encryptor written in Python. Leverages several encryption techniques to avoid detection by EDR at runtime. Outputs a bin file that you can load into a resource before running. The cool thing here is that it also provides C++ snippets for your shellcode loaders, removing the barrier to entry for generating AND loading the shellcode.
EntraFalcon by CompassSecurity
EntraFalcon is an open-source, Powershell-based Entra posture management tool. You give it a global read on your Entra environment, and it'll scan your deployment for risky configurations, identity and entitlements findings, and access configurations. They did a good job of creating an all-inclusive tool to authenticate into your Entra environment, HTML reports, and some risk insights.
Bolthole by rvrsh3ll
This clever Reverse SSH shell framework abuses Microsoft Azure’s ClickOnce deployment model to gain access to a victim network. Once you set up the environment, you send a phishing link to the victim that uses ClickOnce.
ClickOnce is a deployment technology that enables you to create self-updating Windows-based applications that can be installed and run with minimal user interaction.
lol.
sqlmap-ai by atiilla
AI copilot for SQLMap, the legendary SQL injection scanner. You provide an API key, point it at an endpoint, and it smartly tries to perform SQL injection without noisily blasting the endpoint.
LlamaFirewall by meta
Meta’s new guardrail-style LLM security wrapper. It’s cool to see these go open source so you can use internally instead of buying a product.