Det. Eng. Weekly #111 - I'll take 1 trade show with a side of cyber vandalism
Hold the marketing and give me a sprinkle of favoritism
Welcome to Issue #111 of Detection Engineering Weekly!
I’m at RSA this week and it’s (already) been a tiring, rewarding and overwhelming event. I got to speak about supply chain security on Monday, and I’m now meeting customers, hanging out with other researchers and running into new and old friends.
If you spot me on the floor, come say hi and get some Detection Engineering Weekly stickers!
⏪ Did you miss the previous issues? I'm sure you wouldn't, but JUST in case:
💎 Detection Engineering Gem 💎
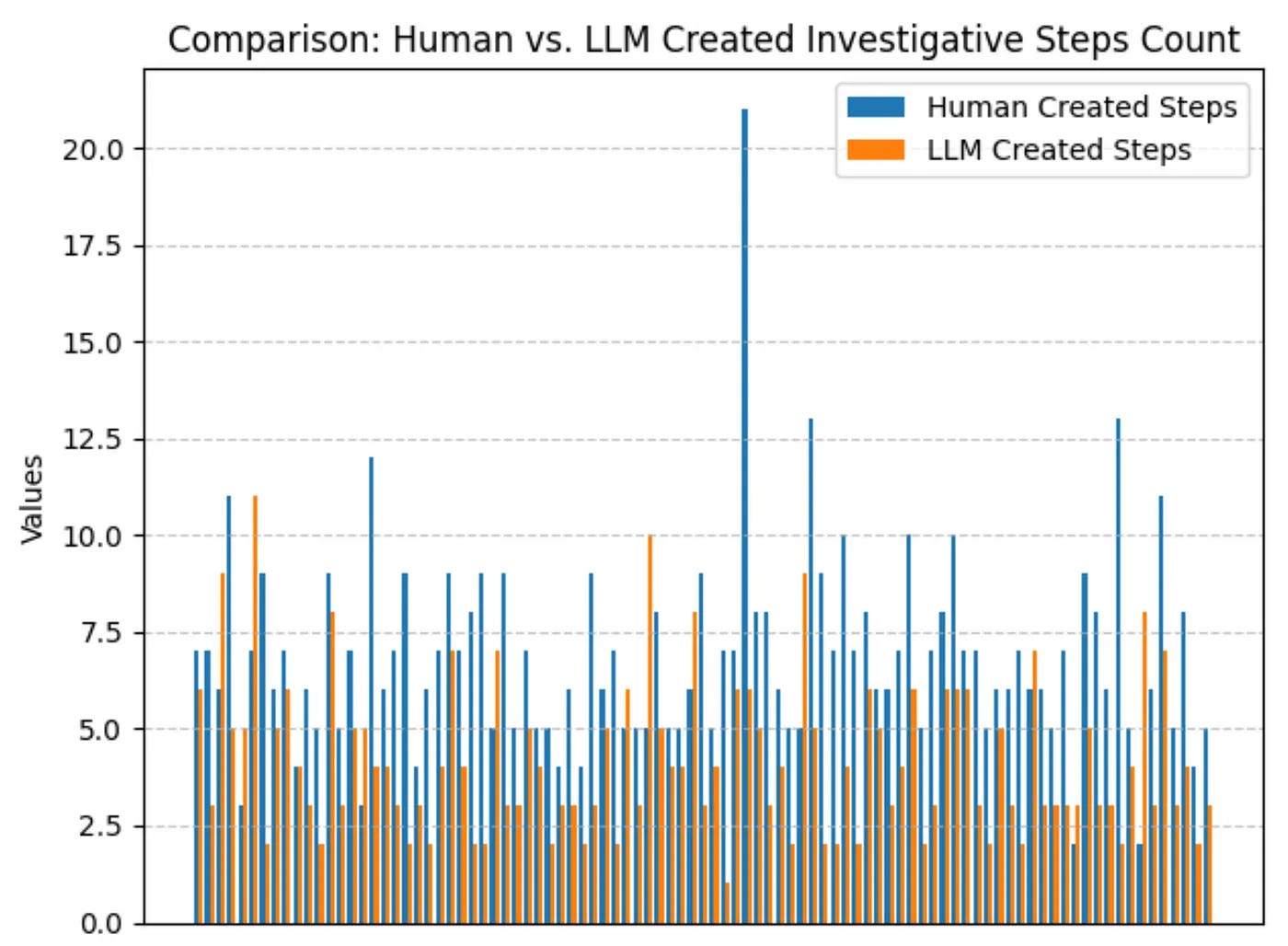
Can We Stop Documenting Our Detections? by Gary J. Katz
The most important things you do day-to-day as a security engineer are often the most tedious. This is mainly because repetitive tasks, such as documentation, aren't meant for a machine, but for another human. If you ship several rules on finding malicious activity in network logs and don't document any investigative playbooks associated with the rules, are they valuable?
Of course not! The investigation is such an essential part of the funnel of fidelity; why stop at alerting? So, if documentation and playbook writing is painful, can anything help with investigations to relieve that pain? Gary asks this question as it applies to LLMs. He performs a super interesting study on how Elastic's open-source ruleset's documentation, written by humans, compares to an LLM's documentation of the same ruleset given only the rule syntax.
The results yield more questions than answers, at least for me. He measured the overlap of investigative steps per rule between humans and LLMs, ranging from 40% to 55%! Gary eloquently points out that it doesn't really say whether playbooks are better or worse between humans and machines.
Elastic's ruleset is tailored for their products and not individual environments, so it's hard to say whether these playbooks make sense in a specific SOC scenario. Two, playbooks can contain generic and non-generic instructions. An example is "Open Workday and confirm XYZ's workstation is within the Finance subnet" versus "Correlate IP addresses with threat intel." Are these helpful steps or not useful? Again, it depends on the environment!
The more I dive into LLMs for security, the more it becomes apparent that you'll be disappointed without anything tailored to your environment. Gary puts a call to action at the end of the post for running his open-source toolset against your ruleset to see how it performs against his benchmarks. He asks the community to send him the results if you can so he can do a follow-up post.
🔬 State of the Art
Because Logs Don’t Hunt Themselves - A Deep Dive into tstats by Sydney Marrone
Sydney is kicking off a sub-series for her THOR Collective Dispatch newsletter focused on technical, bite-sized studies on Splunk queries.
tstats is a great way to investigate slow-running queries inside your indexes, especially if certain fields aren't indexed, and you need to fix your ingestion pipeline to account for it. It's great for initial investigations into sourced indexes and can give you a pseudo lay of the land when configuring the index. She ends the post with a hunt query looking at potentially noisy (or naughty!) Windows hosts bucketed by the hour using tstats.
Measuring the Hunt When You Find “Nothing” by Lauren Proehl
I love reading posts that showcase how a security team can measure success and effectively communicate those measurements to stakeholders outside their organization. One of the most significant problems I see as a leader of security teams is that they often remain in a "bubble," meaning they don't communicate the outcomes of their actions. IMHO, the secret sauce to security career acceleration is communicating impact to your colleagues and leaders.
In this post, Proehl applies this outcome-focused measurement to threat hunting. The exciting thing about threat hunts is the potential to find a baddie, but if you don't find one, then what? According to Proehl, everything from detection and telemetry gaps to control recommendations and hunts originating from CTI or emerging threats is a great way to showcase the impact of a hunt team.
Rulehound by Brendan Chamberlain
Rulehound is an open-source SaaS app that indexes detection rules across several open-source rule repositories. You can search by rule name and quickly identify all kinds of detection candidates for your pipeline. For example, searching for "PowerShell" yields 459 rules across the rule sets.
The Eventlog Compendium by Nasreddine Bencherchali
The Eventlog Compendium is an open-source SaaS app (two in one issue!) that serves as a reference guide for detection engineers, incident responders, and IT admins who need to research Windows Event Logs for analysis or policy deployment. It has everything you need to review EventIDs, ETW providers, MITRE ATT&CK mappings, and even configuration builders.
Tactical Tuning by Combinational Reduction by Brady Stouffer
I don't see enough posts about the thought processes behind tuning a rule, so I was happy to see Brady's post on my feed this week. Rules are like a garden; you have to tend to them daily, except that the garden is an SOC, and you can make another human's life miserable if you deploy a noisy rule.
I'm gonna stick with the theme of gardening here. Within that daily tending, you must prune rules so they aren't as noisy. In this post, Brady outlines his process of pruning and tuning. A common approach is to group by key/values and analyze least occurring values, but that doesn't necessarily mean high-occurring values are false positives. So, Brady goes down this rabbit hole and uses a combination of group-bys to show a more precise and resilient tuning strategy, because through this tuning, you tailor the alerting strategy to the environment itself.
🎙️ Detection Engineering Media
I listened to this week's Three Buddy Problem on the road to RSA, and it didn't disappoint! The first 30 minutes or so featured a lot of good conversations about "AI welfare," a term I've never heard before, and why these LLM firms like Anthropic focus on very academic pursuits outside of their core business.
I appreciated JAG's response to this (it's all BS), but he gave a great counter-example of things we could focus on, such as the policy risks of selling a hosted model to a country that lacks expertise in certain fields of study to help accelerate that program.
I sure hope DPRK never steals one of these :^).
☣️ Threat Landscape
Statement from Matt Hartman on the CVE Program by Matt Hartman
All the hype behind CISA being defunded was inaccurately portrayed, according to Hartman, CISA's Acting Executive Assistant Director for Cybersecurity. With all the cuts going on in the U.S. Government, especially some targeting cybersecurity, seeing the risk of the CVE contract being canceled by CISA is of concern to many of us.
As much as I hate to say it, it shows that the industry moves faster and more efficiently in this specific scenario. I'm not saying we give the keys to the CVE kingdom away to a FAANG company, but rather, we have this public good being provided to us and fueling so many cybersecurity programs and products. So, will we let a "contract administration issue" happen again?
Detecting Multi-Stage Infection Chains Madness by Sekoia TDR and Erwan Chevalie
This is a neat breakdown by Sekoia of an infection chain leading to AsyncRAT. There were many steps to this infection, ranging from the email lure to Cloudflare tunnels and, eventually, C2 communication with AsyncRAT. They outline each detection opportunity along the way and provide the corresponding Sigma rules. It's a great showcase of chaining detections, but more importantly, it shows that a defender really only needs to be right once to start pulling the thread of a security incident.
Phishing for Codes: Russian Threat Actors Target Microsoft 365 OAuth Workflows by Charlie Gardner, Josh Duke, Matthew Meltzer, Sean Koessel, Steven Adair, Tom Lancaster
Volexity researchers uncover several campaigns targeting government officials in the EU using M365 OAuth Workflows. Many of these officials use Microsoft 365 email to conduct official business, and lucky for them, Microsoft has many developer tools that threat actors can use to circumvent traditional controls! A victim is directed to a shared Visual Studio Code space that executes an OAuth workflow for an Authorization token. All legitimate functionality.
The malicious part here is that the shared Visual Studio Code space instructs the user to copy and send the Authorization token back to the attacker, almost akin to ClickFix attacks. The attacker can trade that token for an Access key, which has all kinds of permissions to pilfer the victim's inbox to do spy stuff.
Fire In The Hole, We’re Breaching The Vault - Commvault Remote Code Execution (CVE-2025-34028) by watchTowr labs
watchTowr released another vulnerability writeup, this time for a data storage solution Commvault. If you are interested in vulnerability research, especially in storage and edge devices, or you want to see how these are typically pwned so you can derive some detection opportunities, this is a great post for that!
Commvault is an application that runs on Windows via Tomcat, and ships a Java JAR file to run the application.
Through some decompilation efforts, lots of regex and grepping, and a lucky find for excluded endpoints for authenticated, the watchTowr team went from one POST request to an SSRF to uploading a web shell onto a target box.
Uncovering a 0-Click RCE in the SuperNote Nomad E-ink Tablet by Jack Maginnes
Two vulnerability writeup posts targeting Java apps in one issue! This time, Maginnes and the Prizmlabs team targeted an E-Ink tablet called the SuperNote Nomad. The researchers found an open port on their Tablet and poked at it. Luckily, they found that firmware images were published publicly from the E-Ink company, so they mounted that and decompiled an APK on the firmware to see how the application was structured.
The company rolled its own HTTP server on port 60002, and this server had the functionality to update an image and accept that update from anyone who sends a POST request. They ran into an interesting file-naming race condition, which I won't spoil, but imagine taking notes in class from your E-Ink tablet, and a malicious update appears as a popup right in front of you!
🔗 Open Source
Eventlog_Compendium by nasbench
Eventlog compendium source code for Nasreddine’s “Eventlog Compendium” listed above.
Rulehound by infosecB
Rulehound sourceocde for Brendan’s “Rulehound” SaaS app listed aboved.
detection_documentation_analysis by gjGatos
This repository contains the ipython notebooks and results from Gary Katz’s detection documentation analysis with LLMs above. You can set your OpenAI key, point it to your ruleset, and get results. It’s also setup with langchain, so you can plug and play your LLM provider.
watchTowr-vs-Commvault-PreAuth-RCE-CVE-2025-34028 by watchtowrlabs
PoC of CVE-2025-34028 on Commvault devices. The vulnerability report that yielded this PoC is listed above in Threat Landscape.
GPOHound by cogiceo
GPOHound is a Bloodhound-esque tool that dumps GPO objects from the Window’s SYSVOL share for misconfiguration analysis. These misconfigurations can lead to additional lateral movement and privilege escalation. It integrates directly with BloodHound’s backend Neo4J database, so you can query GPO objects on top of what BloodHound finds.