Det. Eng. Weekly #108 - Can any1 in the IC add me to their Signal group?
Just tryna forward some reels and feelin left out rn
Welcome to Issue #108 of Detection Engineering Weekly!
⏪ Did you miss the previous issues? I'm sure you wouldn't, but JUST in case:
💎 Detection Engineering Gem 💎
Entropy Triage: A Method to Repair Files Corrupted by Failed Ransomware Encryption by James Gimbi
My friend James has been in the incident response and detection field for over 10 years (about the same as me; it turns out we met in college :D ), and I've always loved reading his work since then.
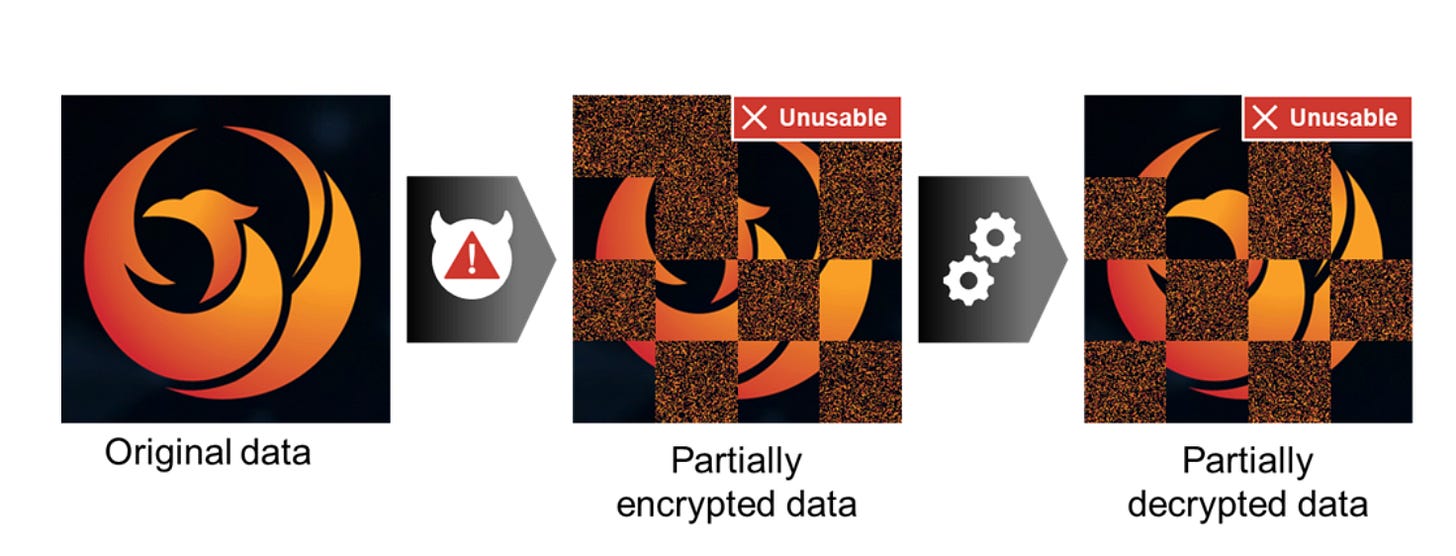
Ok, so, basically, ransomware operators suck. They suck for many reasons, and we can all rant on the ethical nature of their operations. They also can suck at the technical parts of ransomware since they are not crypto experts. So, sometimes when they run an encryptor on a victim environment, they partially encrypt data due to lousy luck, poorly built tooling, or a defender disrupted their operation.
When this happens, and the victim obtains a decryptor, the decryptor can't account for partially encrypted and corrupted files, so the the decrypt operation fails. James put a great visual in the post explaining this:
His research focuses on decrypting partially encrypted and corrupted data from ransomware infections and returning them to normal. He does this by combining the threat actor-provided decryption tool, the decryption key, and some clever information theory techniques.
Leveraging Shannon Entropy, James could measure a potentially encrypted block before and after running the decryption routine. If the entropy was lower after decryption, then it was a successful decryption, and that block was written to disk. If the opposite happens, then he assumes the block was already decrypted and doesn't change the block.
His firm boasts (and rightfully so) an over 90% success rate in using this technique on corrupted files.
🔬 State of the Art
Malware Knowledge Base by Stuart Ashenbrenner
This is a compendium of notes compiled by Ashenbrenner over years of macOS malware research. They slice and dice it in several ways, so you can look into macOS malware by family, threat actor group, or malware type, like info stealer or ransomware. Each entry has news articles linked to the malware and some light annotations.
TCCing is Believing by Patrick Wardle
Transparency Consent and Control (TCC) is macOS' response to insecure or malicious access to sensitive data by users and processes. According to Wardle's blog post, Apple finally shipped these pesky alerts you get when downloading and clicking on something from the Internet into their Endpoint Security ecosystem.
The first half of the blog is an excellent rundown on how TCC works and how threat actors try to circumvent it. He references some vulnerabilities in attacking TCC, but lots of modern macOS malware now just straight up asks you to press accept on the TCC prompt. To log TCC events, defenders had to painfully integrate a logging facility from TCC to look at audit events.
But that is no longer the case. Newer versions of macOS shipped a new event type, ES_EVENT_TYPE_NOTIFY_TCC_MODIFY, and Wardle does the hard part of deconstructing the data structures with some of his own code. The problem Wardle uncovers is that in many cases, the actual binary ran is different from the application requesting TCC permissions (such as Terminal), so we are still kind of left in a blind spot.
Making Detections Great Again by Arun Yadav
This post by Arun Yadav explores the age-old question in Detection Engineering and something I ask in interviews with candidates: what makes a good detection? Here's Yadav's answer:
1.Their ability to unmask the adversary
2.The burden they place on our defenders
3.The disruption they inflict on attackers.
It's a little different from other posts I've seen about the topic because it takes a much more strategic approach to writing a detection rule. Some of the descriptions are familiar, such as achieving reasonable MITRE coverage and building resiliency into rules as threat actors change their tactics.
The Volatility measurement in Part 3 was the most interesting to me: if a detection is volatile, such as detecting bad IP addresses, then it'll be a low value detection.
HexShare by Sharon Brizinov
Have you ever wanted to share a hexdump in a presentation or during a CTF, and struggled to highlight a subsection that is critical to whatever your finding is? Look no further! This is a neat website where you can upload a file, select a section of that file up to 1024 bytes, and use their playground to highlight different sections. You then mouse over the interesting parts and choose colors to magnify whatever you need to show. There are links to share the annotated hexdump., but I couldn't find an export feature for a PNG. A screenshot should be fine though.
** Update **
Sharon responded and pointed out the button right in front of me to export:
Sorry Sharon!
CVE to EPSS | Lookup EPSS data for a CVE ID by Brandon T. Elliott
For those unfamiliar with the Exploit Prediction Scoring System (EPSS), it's a machine learning model developed by FIRST that attempts to provide a predictive score on whether or not a given CVE will result in an exploit. They just released Version 4 at the end of March, though I couldn't find any update post on improvements.
You can use an API that FIRST provides to get an EPSS score, but I found this site to be super easy to use for quick lookups for those who don't want to add yet another chili tool to their arsenal.
☣️ Threat Landscape
The "IngressNightmare" vulnerabilities in the Kubernetes Ingress NGINX Controller: Overview, detection, and remediation by Christophe Tafani-Dereeper, Matt Muir, Frederic Baguelin, Andy Giron and Adrian Korn
~ Note, All of these authors are my colleagues at Datadog, and we are all on the security research team there ~
IngressNightmare was the talk of the town last week, and it was initially discovered, disclosed, and blogged about by the Wiz Research Team. Datadog Researchers pulled apart the vulnerability and identified ways to fingerprint vulnerable clusters. They gave a great breakdown of how it works and how to boot up your vulnerable environment to try it out.
Fake Zoom Ends in BlackSuit Ransomware by The DFIR Report
This blog is yet another excellent intrusion breakdown from the magnanimous DFIR Report. Malspam and blackhat SEO are still things, and this time, the initial access vector was a trojanized Zoom application that the victim downloaded.
The thing that caught my eye on this one was the use of InnoSetup by the D3F@ck loader malware to deploy a malicious Pascal script. During this engagement, many detection opportunities were pointed out. Several post-exploitation frameworks like BruteRatel and Cobalt Strike were dropped multiple times, three or four loader families were dropped, and psexec_psh was used for lateral movement.
A Sneaky Phish Just Grabbed my Mailchimp Mailing List by Troy Hunt
Troy Hunt, the founder, and maintainer of HaveIBeenPwned, self-disclosed a successful phishing attack against him. It specifically targeted his Mailchimp account, and it was a standard attacker-in-the-middle phish kit. He clicked an email that bypassed spam filters, entered his credentials via 1password, entered the OTP code from his authenticator app, and the phishing site correctly sent him to Mailchimp. They registered an API key and exported his mailing list. He only found out when Mailchimp restricted his account for spam reports.
Quickly and efficiently, Troy loaded the same exfiltrated email list into HIBP. He notified people—probably his fastest breach notification ever!
From Contagious to ClickFake Interview: Lazarus leveraging the ClickFix tactic by Amaury G., Coline Chavane, Felix Aimé and Sekoia TDR
Contagious Interview is a cluster of DPRK-nexus activity that finds victim developers who want to interview for a job. During the interview, they install malware like Beavertail and InvisibleFerret. According to Sekoia, there's been a change in TTPs by Contagious Interview, which they dubbed "ClickFake Interview."
The chain is pretty clever. Instead of pointing users to a GitHub repo like before, they point victims to a ClickFake Interview-controlled server to submit their application. Victims eventually visit a page where they socially engineer the victim to enable their Microphone, and they provide a "ClickFix"-style cURL command to run, which infects the user. Their video shows it all in real-time, so make sure to check that out.
Tempted to Classifying APT Actors: Practical Challenges of Attribution in the Case of Lazarus’s Subgroup by 佐々木 勇人(Hayato Sasaki)
This is an excellent follow-up to the Sekoia blog post above.
The author dives into sub-group identification within the Lazarus umbrella. Multiple firms have different names for these sub-groups, including where I work, so keeping track of who-calls-what-what is an important task. I particularly liked reading about the justification of creating subgroups. Attribution does increase costs to attackers, and it helps defenders reason through TTPs without clumping together groups and wasting time building counter-measures on things that don't affect them.
🔗 Open Source
GhidraMCP by LaurieWired
Ok, I’m officially on the LLM train. There’s been a ton of advancements on integrating LLMs into workflows, and MCPs have been popping up everywhere. You can think of an MCP as a standard messaging format that passes requests to use specific functions within an application, such as a search query or in this case, a Ghidra function, using natural language. CTFs are going to be solved by LLMs within the next few years.
SpyAI by DarkSpaceSecurity
This neat spyware implant takes screenshots of a victim's desktop, exfiltrates the screenshot to Slack as a C2 server, and uses an LLM to visually analyze the screenshot to build daily activity.
varalyze by brayden031
Varalyze is a threat intel CLI that combines several data sources for threat intel lookups into one tool. The tool has a cool workflow/multi-use capability to chain lookups together and build a report.
CVE-2025-1974/README.md by sandumjacob
This is a PoC environment for IngressNightmare, all done in Minikube. It's a great way to build and validate detections for the exploit.
rkchk by thalium
This is a pure Rust-based Linux kernel module (LKM) rootkit checker. It checks for 15 scenarios LKM rootkits use to install and persist on a machine. It uses the Linux Rust API, and you have to compile the Linux kernel with Rust support. They tested detections for close to 10 different LKM and User-mode Rootkits and detected all of them!