Det. Eng. Weekly #102 - Explain the Doncic/Davis trade in security terms
You traded all of your Yubikeys for a VPN Appliance
Welcome to Issue #102 of Detection Engineering Weekly!
⏪ Did you miss the previous issues? I'm sure you wouldn't, but JUST in case:
💎 Detection Engineering Gem 💎
Offensive Kerberos Techniques for Detection Engineering by Noah H.
Windows Authentication via Active Directory (AD) is such a rabbit hole. Besides understanding the internals of the Windows operating system and the Microsoft ecosystem, you now have to understand the implementation of the Kerberos protocol. MIT researchers built Kerberos in 1988 (!), actively replacing NTLM as the preferred authentication scheme for AD-connected clients and applications.
It’s also one of the most abused protocols in a victim environment, as an attacker attempts to laterally move and privilege escalate to the keys of the kingdom, the AD server. There are a ton of published red-team articles on how to perform these attacks. Still, this article by Noah is my favorite one on the subject for two reasons: it’s a compendium of attacks with detailed explanations, and there are detection opportunities!
I wonder how much-sunk cost Microsoft has put into supporting this ecosystem in a backward-compatible way. I think of modern authentication and authorization protocols like OAuth and appreciate the simplicity of accessing microservices in a much more.. sane way.
🔬 State of the Art
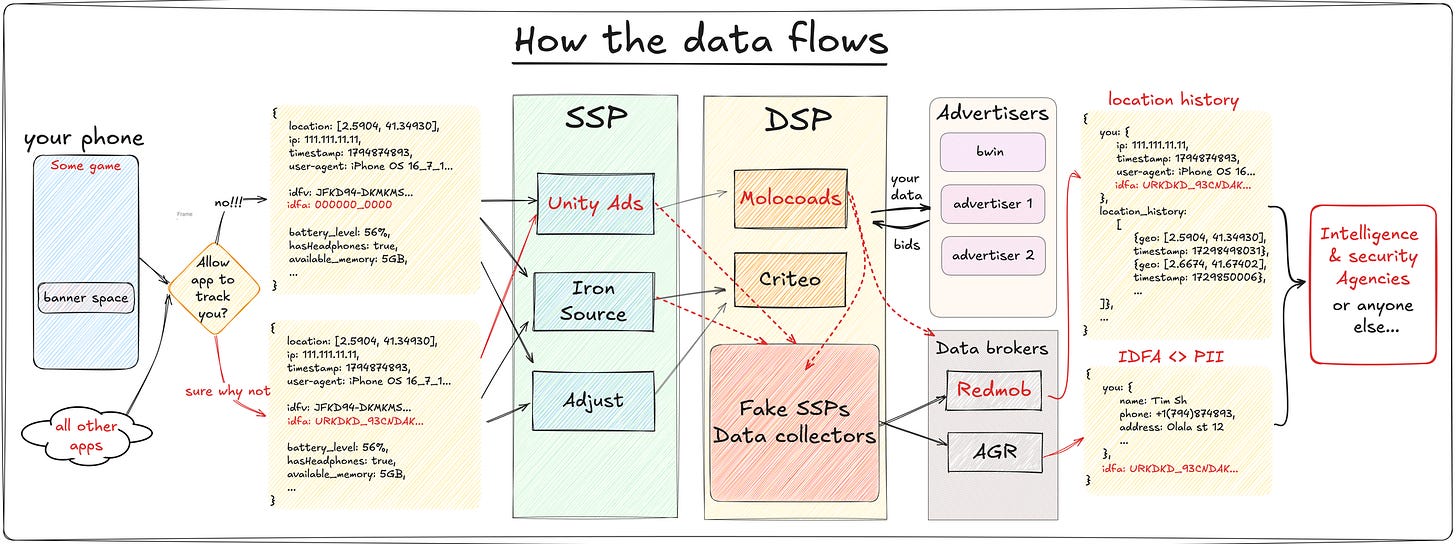
Everyone knows your location: tracking myself down through in-app ads by Tim.sh
I’ve joked over the years about threat intel products, and vendors don’t give enough data to make anything actionable. The real intelligence vendors aren’t in cybersecurity but in marketing.
Imagine near real-time access to a ridiculous amount of PII down to physical location and device type, and you can target clusters of this data and serve them a virtual poster board with whatever marketing or propaganda you want. That’s what a “data-service provider” is, and Tim.sh does a lovely experiment on exposing the Borg-like technologically ruthless ecosystem behind all of this.
With a throwaway iPhone and Charles Proxy, he maps out what you see below in detail. I’m the most terrified of how commoditized and accessible this infrastructure entails. It makes sense why malvertising is such an effective initial access mechanism.
Announcing the Elastic Bounty Program for Behavior Rule Protections by Mika Ayenson, PhD, Samir Bousseaden, Rodrigo Silva, and Jake King
The Elastic Security team announced a bug bounty program for detection rules. The basic rules behind this bounty entail downloading their rulesets, setting up an environment, installing their SIEM or EDR, and testing whether you can perform evasion of the rule. They are running the program in a limited timeline, but really cool to see you can get payouts for evading detection rules.
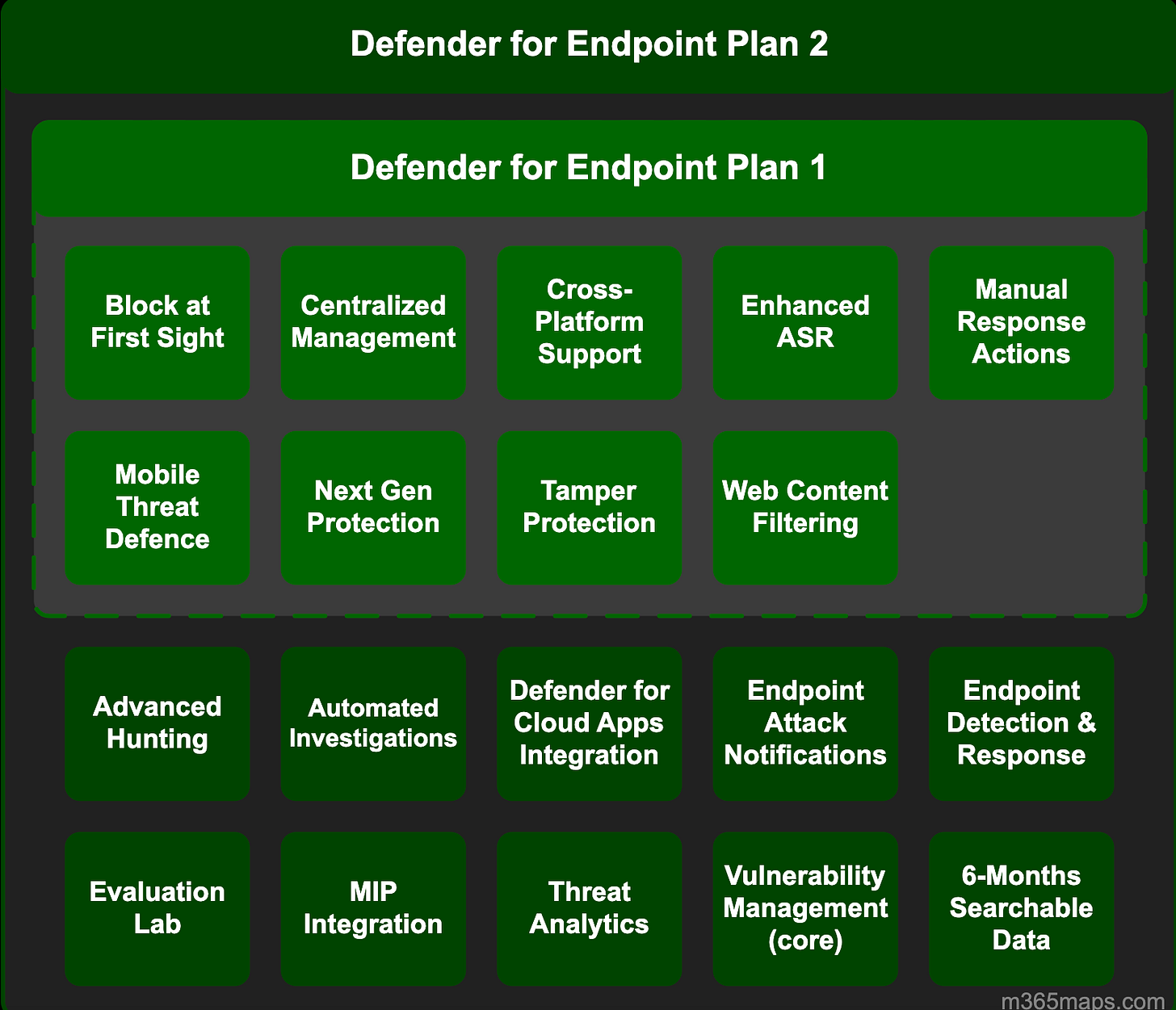
M365 Maps by Aaron Dinnage
Visual map of different Microsoft pricing and packaging for security, logging, and O365 projects. I don’t want to dunk on the author because they provide an IMMENSE service for Microsoft customers. But why do we need someone creating a website dedicated to visuals to help people understand the confusing Microsoft pricing model? Here’s the map for Defender:
Not bad, right? OK, now look at this Entra one:
Insanity!
What Makes a “Good” Detection? by Ryan G. Cox
Since starting this newsletter, I’ve read several “what makes a good detection” blog posts, mainly focusing on the false positive and negative aspects of detection engineering. What I like about this post is that it explores good detections before and after they reach an alert, aka the cost of detections. Of course, you want to tune out false positives and account for false negatives, but the cost of an alert is a much more stable metric (IMHO) that involves false positives and negatives.
Cox includes cost metrics such as visibility from log pipelines and how much it takes to maintain them, the resiliency of the detection generating more or fewer alerts over time, as asks: is the threat even worth detecting compared to my other detections? Capacity planning for your SOC and detection engineers is a business decision as much as a technical one. I think this post has been the most comprehensive in capturing and putting that idea into words.
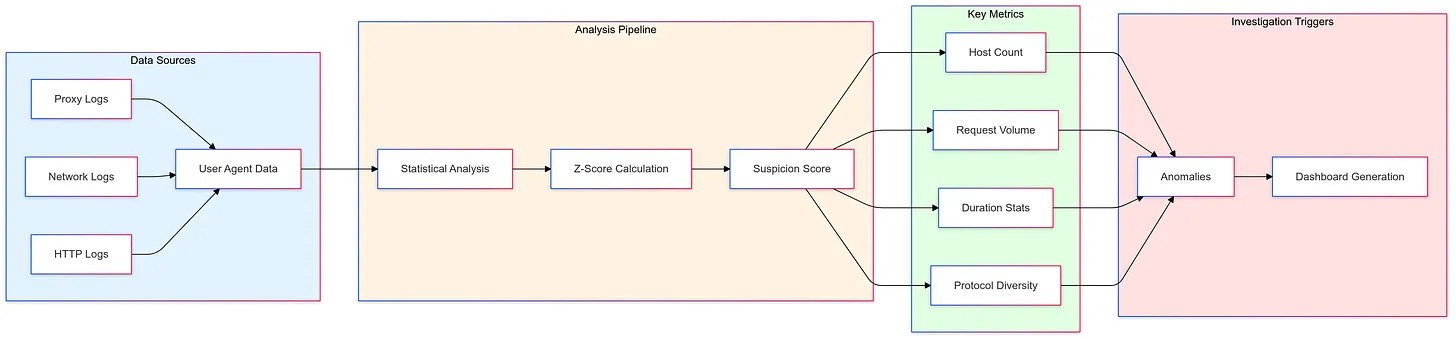
Threat Hunting: Decoding User-Agents for better Insights by Cyb3rhawk
Yay! A detection post using statistics! Cyb3rhawk dives deep into leveraging User Agents for threat hunting, primarily focusing on proxy and network logs. The neat part about this blog post is that it entails looking at several types of baseline, both user agents, and pairing these user agents with hosts. For example, should one host have one, two, or many user agents? How about basing the windows on how hosts communicate with these User Agents?
They also include some excellent visual representations of their architecture, one of them shown below:
☣️ Threat Landscape
macOS FlexibleFerret | Further Variants of DPRK Malware Family Unearthed by Phil Stokes and Tom Hegel
SentinelOne researchers give an update on InvisibleFerret malware and how Apple shipped new rules to block the execution of previous malware campaigns. They uncover a new variant, FlexibleFerret, deployed to victims through GitHub issues rather than job interviews via the Contagious Interview family.
Infrastructure Laundering: Silent Push Exposes Cloudy Behavior Around FUNNULL CDN Renting IPs from Big Tech by Silent Push
This is a fascinating expose of a Silent Push coined cybercrime operation called Infrastructure laundering. The basic idea behind Infrastructure Laundering is that, unlike bulletproof hosts, infrastructure launderers use fraudulent means to obtain IP space from cloud providers and legitimate businesses. Once they get these IPs, they provide a service to cybercriminals to set up their websites, almost like a CDN provides proxying for origin services.
WhatsApp says journalists and civil society members were targets of Israeli spyware by Stephanie Kirchgaessner
Wild story about Meta finding and fixing a “zero-click” vulnerability in WhatsApp. They claim it was used by Paragon Solutions, a Spyware company, to breach approximately 100 journalists and civil society members. Meta contacted the victims and is working with them to remediate the situation. Of course, Paragon declined to comment.
Cracked and Nulled Marketplaces Disrupted in International Cyber Operation by U.S. Department of Justice
#Tangodown baby! Cracked and Nulled got nabbed during a joint takedown dubbed Operation Talent. Both Cracked and Nulled have been around for years. I remember analyzing the capabilities of each forum sometime around 2017. According to the announcement, they both made millions of dollars a year and have affected 10s of millions of Americans throughout their operations.
Unpacking the BADBOX Botnet with Censys by Aidan Holland
BADBOX is an emerging botnet that targets Android devices via what seemingly is a supply-chain attack. Basically, you buy an infected device where the firmware bakes in the BADBOX malware, and it’s infected freshly out of the box. In this post, Holland uncovers BADBOX infrastructure starting with issuer certificate information and finds more hosts with a re-used SSH fingerprint.
🔗 Open Source
lolc2.github.io by lolc2
GitHub repo for the new addition to the lololfarm, lolc2. You can pull the techniques and detections straight from the GitHub repo, or open a P/R with new ones.
LOTTunnels.github.io by LOTTunnels
And another GitHub repo for ANOTHER addition to the lolol farm, lottunnels. Dev tunnels have blown up in popularity for developers and threat actors alike, so make sure to use this for detection opportunities to find malicious ones.
BADGUIDS by mthcht
Interesting repository of malicious GUID strings used by various red team tools. This is just the website’s GitHub repo, but you can access the strings in a mthcht’s separate repository here.
AdaptixC2 by Adaptix-Framework
Yet another open-source adversary emulation framework. Seeing alternatives to Cobalt Strike is always interesting, and it makes me wonder if any of them take off as much as CS. Still, more open source is more better!