Det. Eng. Weekly #100 - Keepin' it 💯
At least for 899 more issues..
Welcome to Issue #100 of Detection Engineering Weekly!
Excuse my language but: holy shit. Issue 100 already? 100 weeks of this madness? Some crude back of the napkin math on content:
100 Detection Engineering Gems, staples that I found to be the most useful for my learning in the space
500 State of the Art blogs, making me and hopefully you all smarter on the latest techniques in this space
500 Threat Landscape updates, making sure we are up to date on latest TTPs and providing job security
500 Open-source links, free to use code bases that can help you stand up and execute a Detection Engineering function
I started linking podcasts and videos in Issue 44
Assuming at most 2 podcasts or videos per issue
56 issues with 2 podcasts or videos = 112 podcasts or videos
At least 1 hour per podcast = 112 hours of listening to detection related podcasts and videos at MINIMUM
And some Substack stats that are really painful to pull because their dashboarding stinks:
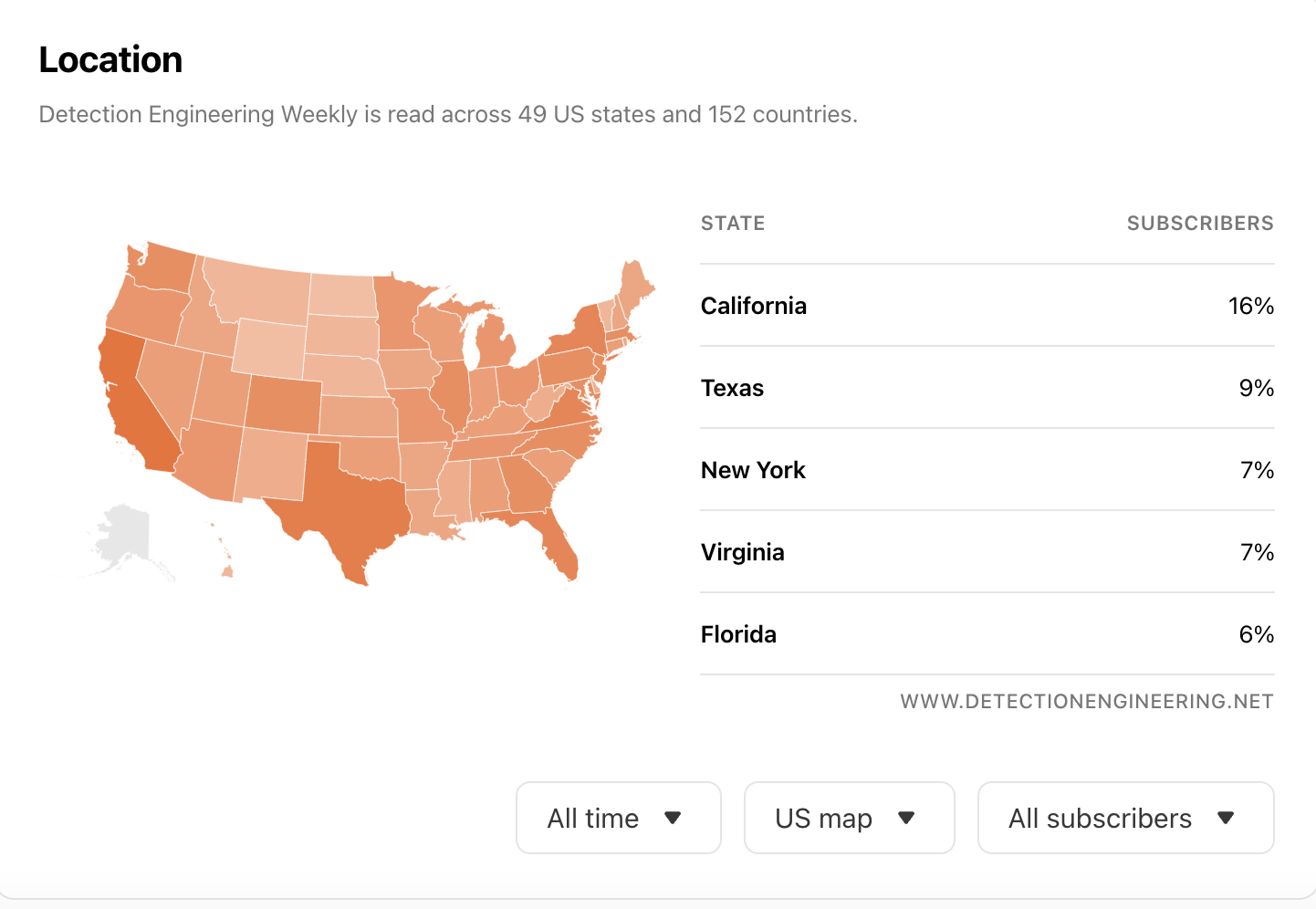
11,468 subscribers
~600,000 unique views, 429,000 of those via e-mail
Subscribers in 49 states (do we know anyone in Alaska? I need this 1 person to subscribe so I can hit all 50)
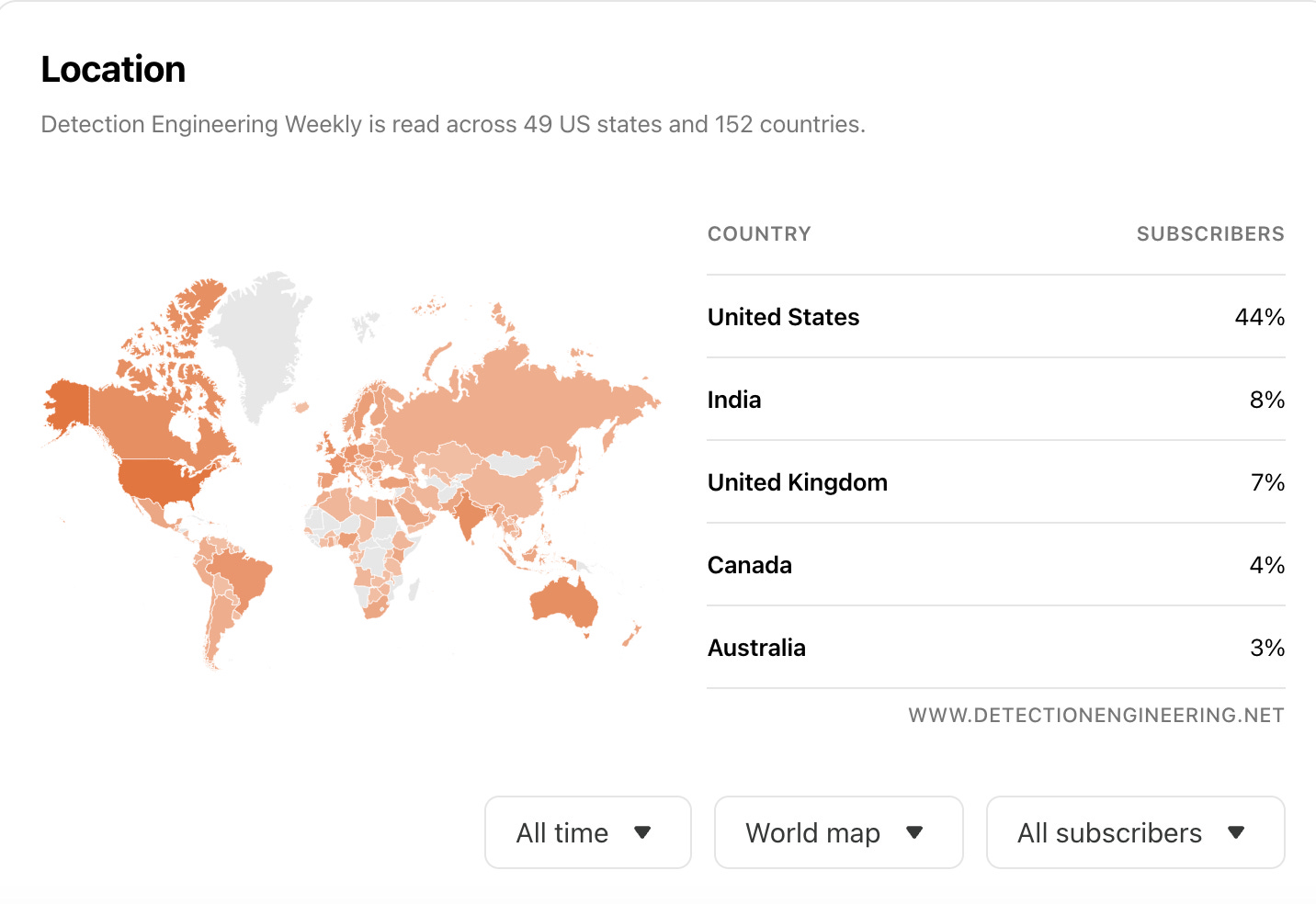
152 countries, US #1, India #2, UK #3, no one from Greenland :(
Pretty cool. Thank you all for reading!
⏪ Did you miss the previous issues? I'm sure you wouldn't, but JUST in case:
💎 Detection Engineering Gem 💎
VMware ESXi Logging & Detection Opportunities by Nathan Burns
ESXi is a critical infrastructure technology for many firms and organizations running an on-premise environment. A local hypervisor that can help manage everything from websites, mail servers, and Active Directory without paying astronomical costs to cloud providers can be a cost-effective alternative for many IT admins. The problem is that it can serve as a control plane over all of your internal critical services. To complicate things, it's a Linux environment, and according to Broadcom, "..is not a General Purpose computing environment," which sounds like they don't want to support AV or EDR.
That being said, there are many detection opportunities with out-of-the-box tools in ESXi, and Burns brings the receipts. I linked their ESXi Testing Toolkit last week and missed this post (sorry!) But it's a gem because it's one of the most complete breakdowns of logging sources, system internals, and detection opportunities I've ever seen for ESXi. There's typical host-level logging in usual Linux suspects like auth.log, but Burns showcases several other sources that leverage undocumented (?) SOAP API and ESXi-specific command line tools
I'd love to see an eBPF agent over this so people can get some form of EDR on top of ESXi, but it sounds like Broadcom doesn't want to support it, so it's up to organizations to implement it.
🔬 State of the Art
Part 16: Tool Description by Jared Atkinson
A (red-team) tool is an arbitrary bucket for tradecraft - Abraham “Jared Atkinson” Lincoln
Someone had to say it out loud, but this is a precise and apt description of a fundamental layer of the Pyramid of Pain that underscores the problem with the Pyramid as a model. Jared builds upon his previous 15 blogs in this series to showcase that detecting a tool isn't necessarily as easy as we think. When you implement any number of techniques in these tools, you pigeonhole yourself in some function chains. Still, you can enable others to leave detection opportunities on the table.
These problems arise when you get asked to detect a tool, and Jared tries to answer this question. What does it actually mean to detect Cobalt Strike, or mimikatz? These tools have all kinds of functionality, so you risk poor attempts at detecting the underlying techniques of the tool if you focus on singular functions of them. This goes down the boundary of what AppSec folks call reachability analysis: you may have a vulnerability inside a library, but do you ever use it? The same thing can be said for tools: you may implement one or many techniques, but do you ever go down each path to find ways to detect them?
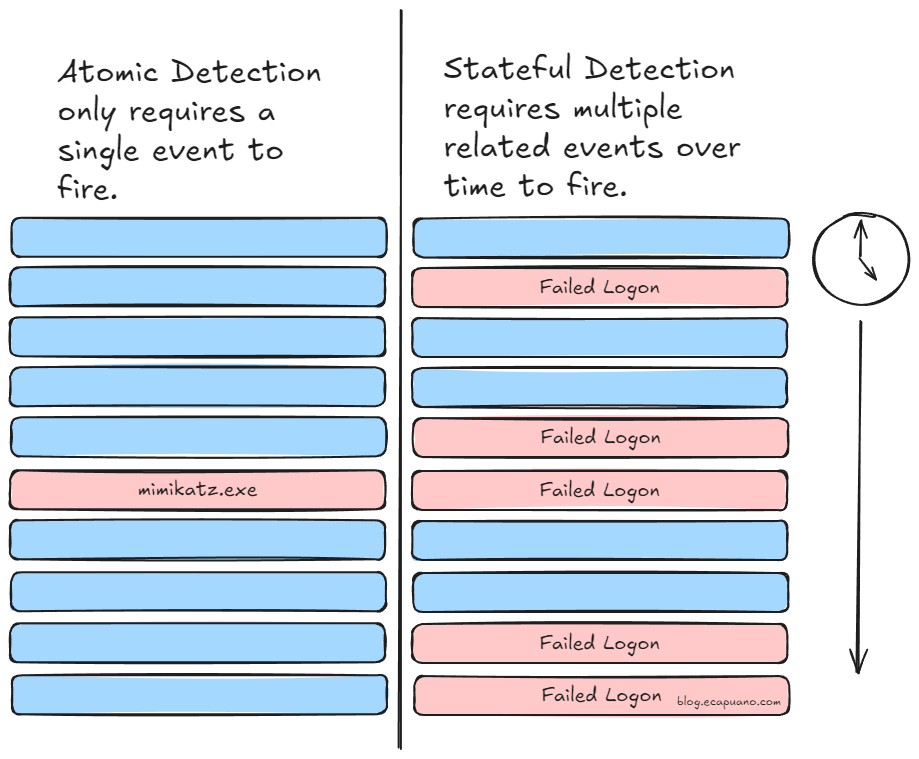
Atomic & Stateful Detection Rules by Eric Capuano
Did you know there are different types of detection strategies? For example, a singular audit log from Slack could indicate malicious activity, such as "this new user just saved a bunch of sensitive documents from a channel they shouldn't be a part of." It's nice when the logic is all bundled in the description. But what does it take to get to that type of precision, and does it always come in a singular log, or could there be many? This is where Eric expands on atomic detections. Instead of a singular event, you could detect many events over disparate sources.
Correlated rules and stateful detections are potent ways to capture behavior across different logs. Eric first gives an example of an atomic detection based on a single process created inside Windows. He then shows how you can use a noisy rule instead of a particular one to correlate the events to something that indicates maliciousness. I'm a visual learner, so seeing how Eric draws out different concepts helped me read and understand his concepts much more quickly than straight text.
Practical Temporal Proximity in KQL by Dylan Tenebruso
Don't let the term temporal proximity scare you. It's a great tool for doing timeline analysis and finding out whether certain events happened within a reasonable distance. For example, when an infection occurs on a host, do you assume a threat actor has hands-on keyboard activity immediately or sometime in the future? This assumption can be helpful for threat hunting and creating detections.
Tenebruso explores this concept in KQL using different windowing and bin options. He throws away most of them because the functions remove the cardinality of when something has happened; you want to know the specific ordering of events if you want to find a threat actor running commands. Tenebruso lands on row_window_session(), which creates Sessions of activity across a specified timestamp. This detection functionality is a practical implementation of Capuano's "stateful detection" blog above.
Introduction to Detection Engineering with Sigma by Isaac Dunham
This is an excellent, up-to-date analysis of the benefits of the Sigma detection engine. Dunham includes several examples for detection engineers or detection-adjacent folks who must work in SIEMs and create or convert rules between formats. They also use several open-source tool examples for the conversion of formats and try to highlight some of Sigma's limitations and ways to get around them. Dunham also includes some later features developed by Sigma, such as pipelines and correlations, to showcase how engineers can leverage it for more advanced.
🎙️ Detection Engineering Media
Another excellent episode by the good folks on Three Buddy Problem. I linked the PlugX takedown in last week’s newsletter, and this podcast focuses on this story for close to an hour, and it’s worth every minute to listen. My favorite point of conversation during the PlugX section is when JAGS (one of the hosts) calls out the reliance that FBI has on partner organizations abroad, and how the U.S. needs to stop making it so hard for security researchers do reduce harm via active measures.
A Commencement into Real Kubernetes Security by Jay Beale and Mark Manning
This was one of my favorite talks at Shmoocon. If you want a deep dive in Kubernetes security and threat detection, look no further than Jay and Mark’s talk on the subject.
☣️ Threat Landscape
Salt Typhoon: the Other Shoe Has Dropped, but Consternation Continues by Natto Thoughts
When you ask a threat intelligence person what their specialty is, it could fall into several categories. Data sources like malware, networks, OSINT or "dark web," and a myriad of other technical fields arise. But you can also slice this discipline into two convenient buckets: cybercrime and APTs. I've grown up in the cybercrime research world, but my recent work at $DAYJOB and this newsletter threw me into the world of APTs.
It's hard to be an expert on APTs because there's a massive cultural component that you must be privy to through extensive experience, or you grew up in that culture. This is why I love reading Natto Thoughts; they have cultural expertise that can get me up to speed on Chinese hacking scenes within the government and in their public discourse. In this post, Natto Thoughts performs OSINT on the latest Salt Typhoon sanctions and unveils the MSS-linked architecture of private companies in China.
Unique 0-click deanonymization attack targeting Signal, Discord and hundreds of platform by hackermondev
This is a super interesting post from an alleged 15-year-old security researcher. The basic premise behind this deanonymization attack is that CDNs leverage various geolocation techniques to serve a piece of static or cached content to an end user.
The attack works like this: if you can send an attachment or image to a target on Signal, Discord, and many other platforms, you can use the CDN architecture to determine which data center served content to the user. This isn't a price geolocation, but you can get a general idea of the closest data center to your target.
InvisibleFerret Malware: Technical Analysis by Mauro Eldritch
This is an excellent analysis of DPRK-nexus malware InvisibleFerret. If you are unfamiliar with this malware set, it’s part of Contagious Interview, and relies on victims to do fake job interviews to install the malware. It’s a nice study for people wanting to do malware analysis since the malware is written in two stages across Node and Python, much easier to read than assembly :).
New Star Blizzard spear-phishing campaign targets WhatsApp accounts by Microsoft Threat Intelligence
Russia-nexus APT Star Blizzard has a new interesting social-engineering attack to get victims off email and into WhatsApp. They email targets with a QR code to a WhatsApp group. The social engineering part here is that the QR code authorizes to "link" the victim's WhatsApp data to Star Blizzard controlled accounts, allowing them to download all the victim data from their app.
🔗 Open Source
cyberbro by stanfrbd
IoC extraction tool for quick enrichments on data you paste in. It takes garbage input (sic), extracts IoC patterns and sends them to various intel services for enrichment.
Not an open-source repository, but a free service ontop of GitHub Pages. I miss the CVE intel feeds from X/Twitter, so it’s cool to see an aggregation of CVE chatter over Mastodon.
baitroute by utkusen
Interesting web-honeypot framework that leverages rules in YAML to impersonate vulnerable services. They wrote 3 separate implementations in Golang, Node & Python so you can pick your poison for deploying the service.
dyana by dreadnode
Dynamic malware analysis is back baby! I’ve been waiting for an implementation of eBPF and containers to instrument an environment and have malicious files run inside of it. The repo claims it can work for lots of filetypes, not just binaries, so it’d be interesting to see how observability instrumentation can provide visibility on top of dynamic malware analysis.
CVE-2025-0282 by watchtowrlabs
Yet another Ivanti PoC repo for remote code execution. It’s not fully gadgeted to beat modern OS-level protections by design, but the accompanying blog writeup is excellent.