DEW #131 - ❄️New EDR bypass❄️, CTI Poverty, AWS Infra Canaries & Hunting in IMDS
🫂GET IN🫂CLICK🫂HUNTING🫂NEWS🫂THREAT ACTOR HARMONY🫂DRAMA🫂RULES🫂IOC JUICERS
Welcome to Issue #131 of Detection Engineering Weekly!
✍️ Musings from the life of Zack in the last week
My new office desk is done, and my office feels so much more organized with better use of space
I learned you can 3D print How To Train Your Dragon toys and stole one of these from my kid, who got it as a present
Got a ticket to DistrictCon, so I’ll hopefully see you some you in person!
⏪ Did you miss the previous issues? I’m sure you wouldn’t, but JUST in case:
🚨 𝗗𝗲𝘁𝗲𝗰𝘁𝗶𝗼𝗻 𝗲𝗻𝗴𝗶𝗻𝗲𝗲𝗿𝘀, 𝘁𝗵𝗿𝗲𝗮𝘁 𝗵𝘂𝗻𝘁𝗲𝗿𝘀, 𝗖𝗧𝗜 𝘁𝗲𝗮𝗺𝘀—𝘁𝗵𝗶𝘀 𝗼𝗻𝗲’𝘀 𝗳𝗼𝗿 𝘆𝗼𝘂.
Join us LIVE on October 7th for “𝗙𝗿𝗼𝗺 𝗧𝗵𝗿𝗲𝗮𝘁 𝗜𝗻𝘁𝗲𝗹 𝘁𝗼 𝗗𝗲𝘁𝗲𝗰𝘁𝗶𝗼𝗻 𝗥𝘂𝗹𝗲𝘀 𝗶𝗻 𝗠𝗶𝗻𝘂𝘁𝗲𝘀 (𝗡𝗼𝘁 𝗛𝗼𝘂𝗿𝘀)” — a hands-on webinar with 𝗱𝗲𝘁𝗲𝗰𝘁𝗶𝗼𝗻𝘀.𝗮𝗶
Presenters: Aaron Mog & Tim Peck from detections.ai
Let’s stop drowning in intel and start deploying smarter.
📅 Save your spot now 👇
🌍 APAC: 10:00 AM SGT: Register🌍 EMEA: 2:00 PM GMT: Register
🌍Americas: 11:00 AM PST: Register
Join @ detections.ai - Use invite code “DEW“ to get started
💎 Detection Engineering Gem 💎
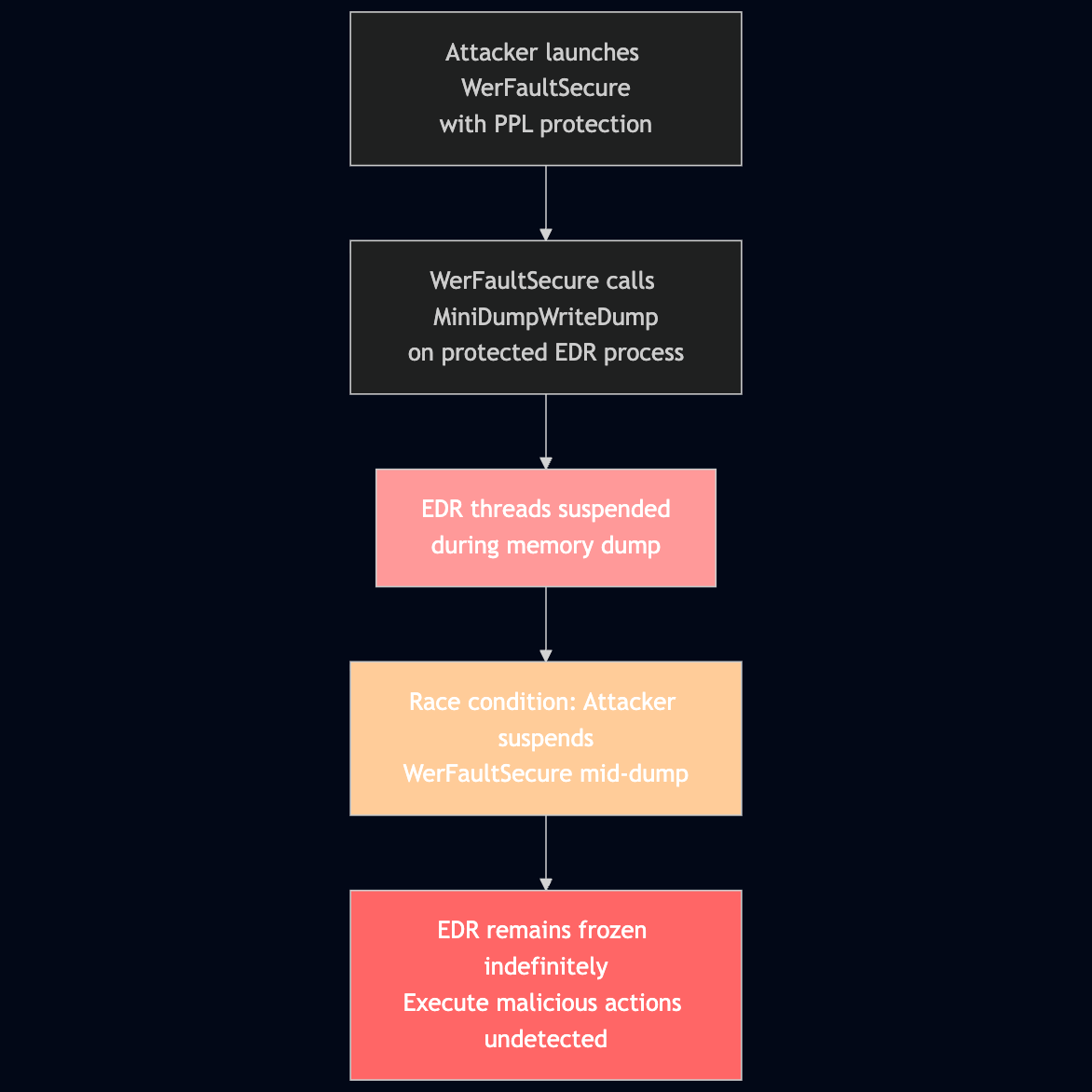
EDR-Freeze: A Tool That Puts EDRs And Antivirus Into A Coma State by Zero Salarium
This is a clever attack against EDR tooling that exploits a vulnerability in Windows Error Reporting (WER), which can cause target processes to enter a suspended state. The race condition, known as EDR-Freeze, exploits a clever method to leverage the MiniDumpWriteDump function, a debug feature in WinDbg, to trick it into thinking it’s creating an object dump of the EDR process. However, since EDRs are protected by ProtectProcessLight (PPL), an anti-tampering method introduced in Windows 8, the attacking process must also be initiated with PPL.
So, the attacker starts the WER executable, WerFaultSecure.exe, and suspends the EDR process via MiniDumpWriteDump function. EDR-Freeze then monitors the EDR to be suspended, creating the race condition. They then suspend the WER calling executable, which means it blocks the EDR process from ever “unsuspending” itself.
It appears that some EDRs are affected, but it was interesting to see the various responses from different companies. For example, Elastic Researchers noted that the technique doesn’t work due to a rule they implemented to block the use of WerFaultSecure.
🔬 State of the Art
Intelligence Poverty and the Commercial Data Economy by Joe Slowik
Cyber threat intelligence (cyber threat intelligence) has been challenging to convince people outside of security of its usefulness in my career. Once you think about the kind of cool stuff you get to do in this genre of security, it seems evident that others would want it. However, I think this bias can cloud people’s perception of the usefulness of a security organization. It’s intangible in many ways, and depending on how mature your program is, it focuses on the “what’s out there” versus “what’s in here”.
Some of this bias is cultural, since CTI was born from the military and spy operations. The stakes are higher when someone’s life is at stake. But, when you introduce the cyber element, it becomes a more frustrating practice in information asymmetry. This information asymmetry is what breeds the market and vendors to sell it: they have data that you don’t.
This is why Joe’s post here is so timely and relevant (just like threat intel!) Many people, including myself, are using VirusTotal (now Google Threat Intelligence) this year. When a company has a monopoly on crowdsourced and expert-created cyber threat intelligence data, it can essentially charge what it wants. According to Joe, this economy of scale creates an “intelligence poverty” for those outside large organizations with a budget to compete.
It makes it even harder for people trying to break into the industry, or for those who do it as independent researchers, to take advantage of data that can be the difference between a breach discovery and not. I really wouldn’t know what to recommend for people who want to do more OSINT-style CTI using these platforms. I’m fortunate enough to be a consumer of these platforms or to have been given researcher accounts. Still, this commercialization may force new analysts to work in fewer places than before.
Our plan for a more secure npm supply chain by Xavier René-Corai
GitHub’s Director of Security Research published a post about GitHub’s response to the the last several weeks of supply chain attacks against npm. The biggest offender, the Shai-Hulud worm, demonstrated how fragile some of these ecosystems can be in terms of security. The open-source community reacted swiftly, starting to analyze the malware code and issuing warnings to GitHub. However, according to René-Corai, GitHub itself needs to take stronger action against these types of attacks.
The GitHub security team is moving towards three publishing options, which are a combination of reducing long-lived publishing tokens and “Trusted Publishing” via means like 2FA. They are also removing several publishing options, and some seem harder than others to implement. For example, they recommend moving 2FA away from OTPs to FIDO-based 2FA, but that can be cost-prohibitive or can be a logistical nightmare to get implemented.
IMDS Abused: Hunting Rare Behaviors to Uncover Exploits by Hila Ramati and Gili Tikochinski
Wiz researchers Ramati and Tikochinski perform a threat hunting deep dive on unusual IMDS usage across their customer environments. IMDS is a beast of a service - without instance metadata, it’s much harder for applications to understand configuration and service data related to the infrastructure they are running on. It’s run on 127.0.0.1, so theoretically, only the applications and the instance can access the service.
This configuration service is an attractive target for attackers, so if they can devise creative ways to access the API, they can use it to steal credentials and move from the instance to the cloud environment. Attackers, unlike services and code, don’t usually fall in the behavioral patterns of accessing the service, so this is where Ramati and Tikochinski start to hunt for compromises.
Once they baselined cross-customer usage of IMDS, they found three compromises related to N-day exploits against various services. I feel that threat hunting is primarily about baselining behavior and identifying outliers, and this blog is a great demonstration of that.
Introducing the AWS Infrastructure Canarytoken by Marco Slaviero
This is a neat feature update from Thinkst Canary, one of the OG companies offering canary token capabilities to security teams. Free-tier and paid users can now leverage their AWS Infrastructure Canarytoken, which is a specialized feature that deploys canary infrastructure. It leverages a combination of AWS permissions, Terraform files, and some special sauce to “learn” your AWS environment and deploy what it thinks is the best canary-style cloud resource. There are two required cross-account integrations: one involves giving temporary access to Thinkst so they can “learn” your infrastructure. The second is a long-term cross-account access that sends your CloudTrail events from the canaries to their main AWS account for alerting and processing.
☣️ Threat Landscape
I’m posting two quick-hit podcast episodes from friends of the newsletter, The Three Buddy Problem.
In this interview, Ryan & Juan interview Aurora Johnson and Trevor Hilligoss from SpyCloud. They gave an overview of a Com-like community in China that performs similar harassment and insider threat style crimes. The difference between this group, dubbed “Internet Toilets” (and the name of their talk), and The Com, is the access to much more persona data due to corrupt officials in local Chinese governments.
This episode is a 12 year lookback on Mandiant’s first ever threat report on APT1. This was a pivotal moment for cybersecurity as it showed how much visibility that private firms possess and how it can overlap nicely with government spy operations. I was 1 year into my career when I first read this report and I was blown away. I entered my first threat research job that same year and the rest is history :).
That Secret Service SIM farm story is bogus by Robert Graham
The big news last week involved the Secret Service busting a SIM farm. The PBS story I linked here claims it could have been used to “collapse telecom networks”. One of the agents had a quote suggesting that a nation-state might have run it.
Several news outlets started poking holes at that claim, and Graham’s piece here points out why. A possible reason why it sounded like a nation-state operation was it financial scale, but also the lead that led to the farm involved a text from this possible “spam farm.” It’s kind of like saying AWS was responsible for a nation-state hack from a China-nexus actor because it originated from an AWS IP.
September 26 Advisory: SNMP RCE in Cisco IOS and IOS XE Software [CVE‑2025‑20352] by Censys Security Research
The Censys team’s threat advisory on the latest Cisco vulnerability provides valuable information on the Internet exposure of these vulnerable devices. A specially crafted SNMP packet can lead to a stack overflow on these 192,000 devices. The prerequisite here is that the attacker must be authenticated to the device. A guest account or a low-privileged account can initiate the attack and get a DoS, whereas a high-privileged account can get RCE to pivot into internal networks.
Canary tokens: Learn all about the unsung heroes of security at Grafana Labs by Mostafa Moradian
Grafana’s Security Research team published this post as a follow-up to their security incident they experienced in May. I really enjoy reading about lessons learned from companies that suffer an incident like this, because firms tend to be risk-averse and not publish details. The follow-up by Moradian involves the use of canary tokens in their infrastructure to identify leaks in their source code.
The team had tokens placed throughout their codebase, and the incident involved exfiltrating their codebase during the attack. Logically, the threat actor leveraged TruffleHog to scan the codebase for exposed secrets. TruffleHog can sift through code, configuration files, and even code commits. You can configure TruffleHog to check the validity of the secret, so it’ll reach out to the various service platforms and look for a response indicating that the secret is live. Once the actor reached out to AWS, it issued a critical alert to Grafana’s Detection & Response team, and they were able to identify the repository from which the secret was stolen.
These tokens offer a cheap and effective way to get some high-fidelity alerts, especially in the case of exfiltration, such as what happened to Grafana.
🔗 Open Source
acquiredsecurity/forensic-timeliner
Security incident timeline builder for DFIR investigators. It can clobber output from several forensics tools, such as Chainsaw and Hayabusa, combines them into a singular format and it creates a nice queryable timeline. It has a GUI that looks a lot like Wireshark which I got excited about :).
gabriel-sztejnworcel/pipe-intercept
This is a neat named pipe interceptor for Windows that leverages WebSockets so you can view named pipe communication via tools like Burp. You specify a target named pipe via the command line argument, connect to the WebSocket via your preferred tool, and see the live IPC traffic over the wire.
awslabs/amazon-bedrock-agentcore-samples
Amazon recently launched AgentCore, their service providing agentic infrastructure. I linked their samples here because it seems pretty straightforward to get a full agentic infrastructure up for security use cases. For example, you can load in system prompts for security triage, leverage S3 as a vector database and upload runbooks and rule descriptions, and connect to their MCP servers for telemetry querying using natural language.
Memory acquisition tool for Linux. You compile it as a binary, load it on a target system and capture memory for offline analysis. Has some native functionality to upload to Azure blob storage. Uses the LiME output format once retrieved, though I’m unsure if Microsoft devs read that LiME is no longer being developed.