Detection Engineering Weekly #35 - Hacker Summer Camp Edition
Good Luck, I'm Behind 7 Burner Phones
Welcome to Issue #35 of Detection Engineering Weekly!
This is a special edition of my newsletter, where I'll replace "threat landscape" with my curated pick of talks @ BlackHat/DEFCON. I tried to mark talks and events that have a Detection Engineering flair.
If you see me, come and say hi! I'll most likely be wearing Datadog gear on Friday/Saturday and have 200 Detection Engineering Weekly stickers to give out, courtesy of the Prelude team:
This week’s recap:
💎 by Joe Slowik on navigating the sh*tstorm of vulnerabilities in the newscycle
MITRE ATT&CK for LLMs
Insights into red team operations and TTP adjustments by Will Schroeder
Micah Babinski invites all of us over to search-ms, WebDAV and chill
SecureWorks on detection opportunities with SharpHound
🫵 Hey you! Do you have a blog post, social link, or open-source tool you want to see in this newsletter?
Leave a comment below or email me techy@detectionengineering.net
💎 Detection Engineering Gem 💎
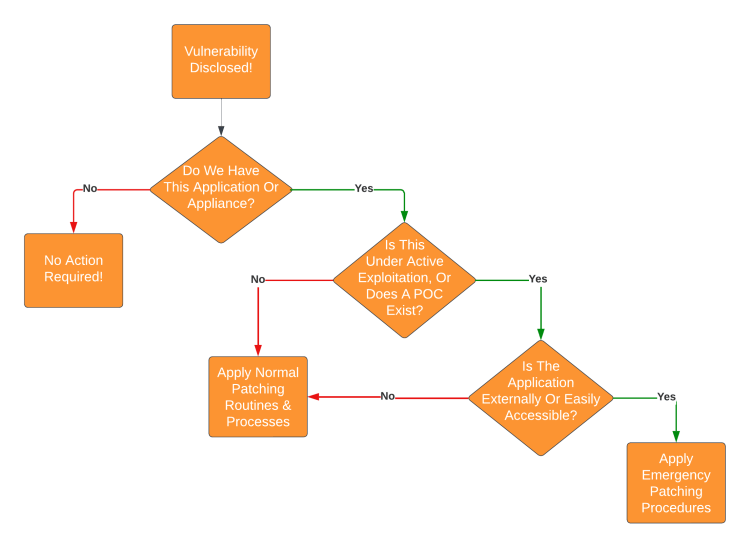
Attaining Focus: Evaluating Vulnerabilities In The Current Threat Environment by Joe Slowik
This is Joe Slowik's second post on this newsletter and second 💎! This post details how the emergence of "celebrity vulnerabilities", the vulnerability news cycle, and the lack of process in managing the vulnerability news cycle can hinder a security operation to the point of burnout. Now, Slowik did not use the word celebrity here, but I see how the onslaught of vulnerabilities with the shakey-at-best scoring system (looking at you, CVSS) can make us overcorrect.
When a problem emerges, I typically respond with three paths forward: build something, hire people, or change the process. Luckily, Slowik suggested a strategy to manage emerging or celebrity vulnerabilities, and I really like his threat-based approach. Explaining it won't do it justice, so please read it, but I attached his flowchart below:
State of the Art
MITRE ATLAS by MITRE
For those of you going to hacker summer camp, get ready to have vendors shove AI and LLM solutions in your faces. One way we can "fight back" against the marketers is to take a red-team approach, so why not study up on ATLAS? This is MITRE's new "ATT&CK MAP" but for ML systems. I'd like real-world examples of threats that successfully exploited models using these techniques.
Challenges In Post-Exploitation Workflows by Will Schroeder
Interesting post by Schroeder from Specter Ops describes how red team tactics and techniques need to change as defenses get better. Overall this post should encourage detection engineers and people on the "blue" side of the equation. The most intriguing section, "Mining Document Stores," shows how red teams value internal file shares and wikis (looking at you, Confluence) during engagements. We've had a few posts on this newsletter about Confluence tools, vulnerabilities, and ransomware.
Search-ms, WebDAV, and Chill. by Micah Babinski
In this blog, Babinski provides a detection engineer's point of view to a Trellix report on threat actors who combine WebDAV and search-ms to phish end users. TL;dr, through some UX confusion, actors can make a website that you can explore as if you are viewing files on your local Windows machine. The best part? Tons of detection opportunities throughout the blog, with some rules at the end!
What's missing before the 'One Metric That Matters' in Threat Detection? by Alex Teixeira
A significant change in a metric value should drive action.
Concise words from Alex on this post about metrics in Detection Engineering! I once listened to a talk from a network engineer who helped build Fastly's CDN. He equated managing a CDN to operating a ship at sea. The ocean is a dynamic environment, and things can change and you are constantly adjusting. It was an apt analogy that we can apply to our field.
We tend to shortcut metrics, so Alex helps provide a 3-step process in creating, well, process, to develop reasonable metrics versus bad ones.
Sniffing Out SharpHound on its Hunt for Domain Admin by SecureWorks Counter Threat Unit Research Team
SharpHound is a C# based data collector for the BloodHound toolset. Like all red-teaming tools, this tool yields detection opportunities as the red team operator tries to gather information about the AD environment. In this post, SecureWorks details some network and event tracing detections when looking for SharpHound executions on your environments. Remember the Pyramid of Pain? Detecting the toolset can help create forward-looking and resilient rules for your detection rules!
Hacktivists: Liars and Morons by BushidoToken
BushidoToken provides a case study on three recent Hacktivist "incidents" and warns others about the risk of misinformation from these incidents. All three incidents they listed have a propaganda component since they are all related to the Russia-Ukraine war. With hacktivism, I always try to assess motivation and work backward from there. The story is more important than the incident or hacks itself, as it helps bolster an image on either side of a conflict.
Hacker Summer Camp
Blackhat
Wednesday
Reflections on Trust in the Software Supply Chain by Jeremy Long
Fast, Ever-Evolving Defenders: The Resilience Revolution by Kelly Shortridge
Nothing but Net: Leveraging macOS's Networking Frameworks to Heuristically Detect Malware by Patrick Wardle
Thursday
What Does an LLM-Powered Threat Intelligence Program Look Like? by John Miller and Ron Graf
Uncovering Azure's Silent Threats: A Journey into Cloud Vulnerabilities by Nitesh Surana, Magno Logan and David Fiser
Evading Logging in the Cloud: Bypassing AWS CloudTrail by Nick Frichette
Seeing Through the Invisible: Radiation Spikes Detected in Chernobyl During the Russian Invasion Show Possible Evidence of Fabrication by Ruben Santamarta
Defcon
Friday
DEFCON Man Conference:
Cloud Village:
The Dark Playground of CI/CD: Attack Delivery by GitHub Actions by Yusuke Kubo and Kiyohito Yamamoto
From Service Catalog Admin to Account takeover: Privilege Escalation with Service Catalog Launch Constraint by Sarachai Boonyakiat
Blue Team Village:
Security Engineering for Adversarial Emulation and Red Teaming by Scott Brink
SOC Panel: Finding, Keeping, and Caring for the Best People by Carson Zimmerman, Alissa Torres, Christopher Crowley and Russ McRee
Saturday
DEFCON Main Conference:
The GitHub Actions Worm: Compromising GitHub repositories through the Actions dependency tree by Asi Greenholts
Lions and Tigers and Fancy Bears, Oh My!: A Cautionary Tale for our Cyber Future by Jen Easterly and Scott Shapiro
AppSec Village
Hunt the Hacker - Detect compromises in your repositories! by GitGuardian
Not All Alerts Are Born Equal: Insights from AppSec Experts on Prioritizing Security Alerts by Shahar Man, Trupti Shiralkar, Kunal Bhattacharya and Joe Christian
Cloud Village
What the Function: A Deep Dive into Azure Function App Security by Karl Fosaaen and Thomas Elling
Security Logging in the cloud, trade-offs to consider and patterns to maximise the effectiveness of security data pipelines by Marco Mancini
Sunday
DEFCON Main Conference: