Detection Engineering Weekly #15 - Emotet's Return
Last week's news and how-tos in the art and science of Detection Engineering
Welcome to Issue #15 of Detection Engineering Weekly!
This week’s recap:
A practical lab to boot up your own Detection-as-Code pipeline from Brendan Chamberlain
Azure CLI and LOLBAS can speed up your Azure detections by inversecos
Another take on Detection Backlog design, Microsoft with some detection and hunting updates, and a runbooks primer
Emotet rears its ugly head, Netwire gets its head cut off, and a Plex vuln inside CISA’s KEV
Explain Detection Engineering to your CEO: Feature #8 -
Note: This submission requested no attribution.
Finding common cyber attacks seems to be a “no brainer,” but I have been the victim of jumping directly to the coolest and sexiest attack because my lizard brain likes shiny objects. It seems good business practice to recommend covering 80% of the common stuff first, with the rest of your time finishing the remaining 20%. This is the first submission that has a DFIR angle as well. If we want to recover quickly, we need to make sure the proper controls and logs are in place to reconstruct these sophisticated attacks. Bravo, unknown!
💎 Detection Engineering Gem 💎
Practical Detection-as-Code by Brendan Chamberlain
Many of the gems I post are topical blogs about concepts in Detection Engineering, but I’ve yet to post a practical implementation of Detection Engineering! I love this post by Chamberlain because it walks you through setting up a pipeline of Detections-as-Code using open-source tooling. THIS is how you scale a detection operation!
State of the Art
Azure Command Line Forensics - Host Based Artifacts by Inversecos
This post is a great example of using lessons learned from DFIR engagements and applying similar methodologies to building detections. Just like on-prem, many Azure-based compromises use binaries and tools already installed on the target system or environment, aka LOLBAS. Lots of detection opportunities here!
Intelligence to Risk Framework by Recorded Future
This paper defines a framework for business risk recommendations, focusing on the private industry. I like what Recorded Future did here - they are meeting the private sector where they are, not trying to bring them to some model that works for the government. They acknowledge that the public sector is very good at this translation. In contrast, some translation is lost in the private sector due to a lack of intelligence knowledge and problem space. If the government fails to use intelligence effectively, lives could be at stake. If a business fails to use intelligence, it may impact business.
A Research-Driven process applied to Threat Detection Engineering Inputs by Alex Teixeira
A continuation, or really evolution, of a post made by Teixeira on how to drive a detection backlog. It’s à la carte, meaning you can pick and choose from this process whatever fits your organizational model and then implement it accordingly. You can compare this methodology to others, such as Prager and Leidy’s Prioritization of the Detection Engineering Backlog, or a neonprimetime’s tweet thread on using Agile for Detection Engineering & Threat Hunting.
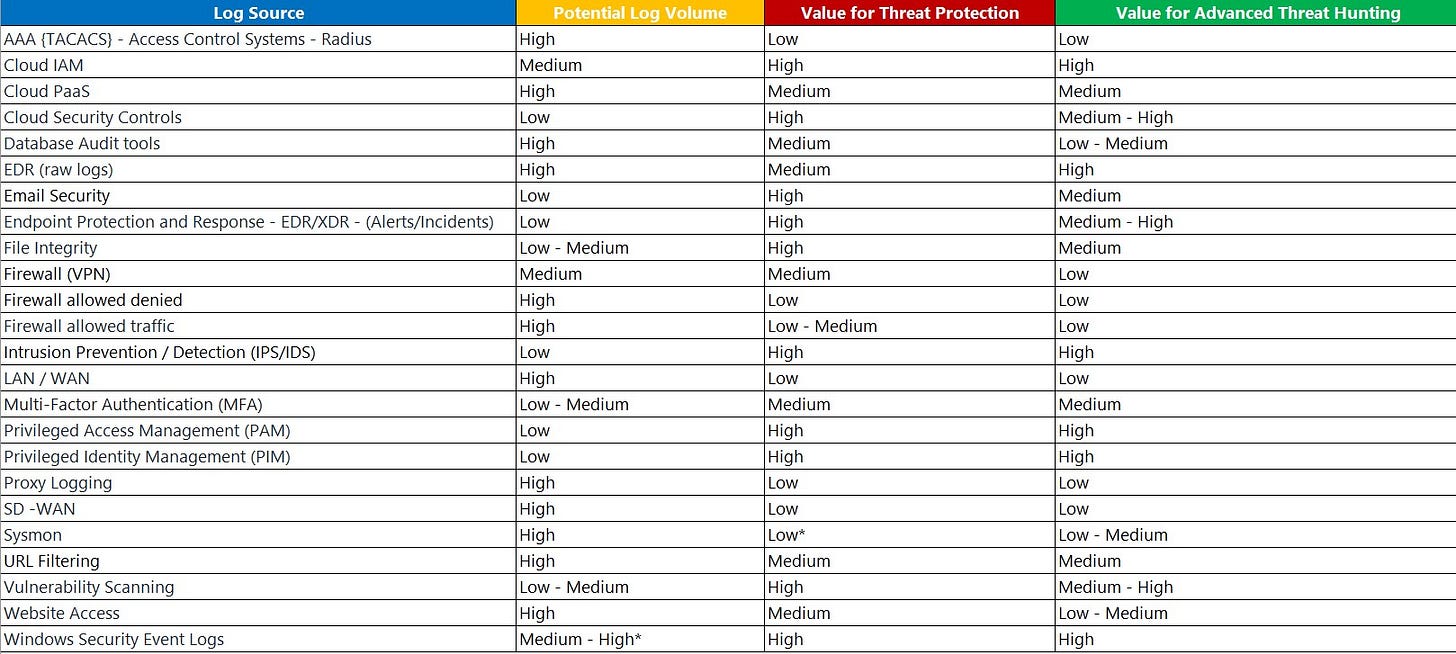
What should I log in my SIEM? by Andrea Fisher
Short and sweet post on what should go into a SIEM and what should not. I appreciate Microsoft’s dogmatic definition of SIEM, and it seems they go to great lengths to describe what is useful and not useful inside one. My favorite nugget is at the bottom, and I hope it’s stored somewhere besides a picture on a blog:
Token protection in Azure AD Conditional Access by MicrosoftGuyJFlo
Exciting feature release from the Microsoft team on token protection. The basic premise is that when a user registers a device for the first time in Azure AD, a token identity is cryptographically bound to the target device. So, when that token (not if) is stolen, maybe via an infostealer like Redline, Agent Tesla, or any of the 232 “for educational use only” open source stealers on Github, etc., the stolen session cookie can’t be reused in your environment. Super high-value alert right there!
A comprehensive synopsis of 217 subdomain takeover reports by Alana Witten
Subdomain takeovers have a lot more impact than defacement or hacktivism. In this post, Witten analyzes 200+ subdomain takeover reports, and notes that many of these led to an intrusion in a host or cloud environment. Of note, accessing IMDSv1 to steal EC2 Metadata Credentials is still a largely deployed technology amongst AWS customers.
Cybersecurity Monitoring and Detection Lab PT1 by Jv Cyberguard
I wanted to highlight this post because I thought it was very thoughtfully laid out, and comprehensive (this is part 1 of 6). It’s good to see newer folks in the industry try their hand at detection labs. Building a detection lab for learning is no small feat, so if you want to see how Cyberguard constructed, deployed, and tested its lab, this is a great piece of content. I particularly like how they create a hybrid environment between local AD and Azure AD.
Runbooks by magsther
This post was not written by a security professional, but by an SRE professional. I’ve always been fascinated by how SRE orgs are so good at keeping a ship afloat, and even better at documentation and runbooks. You should look at how they describe a runbook and see the very similar terminology between security and ops.
Detection Engineering on Social Media
Threat Landscape
Emotet Again! The First Malspam Wave of 2023 by Simon Kenin
Ivan, the Emotet botnet herder is back. If you haven’t researched this botnet family, you should go down the rabbit hole. Emotet started from humble beginnings as banking malware and graduated into a prolific loader and initial access vector for ransomware families. According to Kenin’s research, Ivan has not yet caught onto the OneNote hype, still using malicious word files, but I’m sure they’ll update soon enough.
Microsoft OneNote to get enhanced security after recent malware abuse by Sergiu Gatlan
Interesting update from the Microsoft 365 team: they are adding updated protections to OneNote files being abused by malware authors in the wild. According to Microsoft, it will be GA in April 2023, and that:
Users will receive a notification when the files deem dangerous to improve the file protection experience in OneNote on Windows.
An FBI “most-wanted” malware domain seized by the DoJ! Netwire has a lengthy history of being advertised as a remote assist tool and has been attributed to all types of campaigns, from APT espionage to crimeware.
IceFire Ransomware Returns | Now Targeting Linux Enterprise Networks by Alex Delamotte
It may not be the year of the Linux desktop, but could it be the year when Linux ransomware takes off? In the post, Delamotte notes a variant of IceFire targeting a vulnerable version of IBM Aspera Faspex on CentOS hosts. The variant follows all of the runbooks from ransomware developers: Tor onion site, configurable usernames/passwords for victims, and a nice note to introduce itself.
One interesting observation Delamotte has at the end is that Linux-based ransomware variants have relied more on vulnerabilities in software as an access method rather than traditional phishing or drive-by downloads.
CISA Adds Two Known Exploited Vulnerabilities to Catalog by CISA
Two vulnerabilities in Plex and XStream have been added to the KEV list by CISA. Interesting timing given the news about LastPass and one of their core dev’s Plex server being popped.
DEV-1101 enables high-volume AiTM campaigns with open-source phishing kit by MSTIC
Attacker-in-the-middle kits (I’ve also seen these called puppeteer kits) are clever constructions of phishing websites where the attacker interacts with a victim as they enter TOTP codes into a phishing website. The basic premise is that the kit steals usernames and passwords and then provides a prompt to the victim, when the attacker inputs the stolen credentials into the real site, they are presented with the same prompt. The victim inputs their TOTP code into the kit, which is then proxied to the attacker, who then logs into the victim account. Good to see Microsoft looking at more of these!
Open Source
PSBits/OfflineSAM/OfflineAddAdmin2 at master · gtworek/PSBits · GitHub
Interesting use of on-system DLLs to create administrator accounts on Windows systems while completely offline.
Crawlector: a threat hunting framework designed for scanning websites for malicious objects
Write Yara rules, scan websites, store results, and go hunting! This tool was introduced in a talk by the researcher. It might be useful when you are threat-hunting or analyzing criminal infrastructure.
IAM Ape by Orca Security
Interesting approach to Amazon IAM policy interpretation and consolidation. IAM Ape will connect to your account via whatever AWS profile you pass it, download your IAM roles, and combines them to present you with a single policy with all the permissions. Good way to interpret the complicated mess known as Cloud Security Provider Identity Management 🙂
Secret Bench by setu1421
Massive dataset of manually labeled secrets from hundreds of Github repositories. You can use this to investigate and emulate secrets leakage across your organization.
Awesome Detection Rules by jatrost
Another “awesome” Github repo that aggregates public datasets of detection rules. Make sure to bookmark this one so you can get started quickly on public rulesets!