Det. Eng. Weekly #106 - Have you said thank you once..
..to your friends, family or loved ones? Go do it now and come back
Welcome to Issue #106 of Detection Engineering Weekly!
📣 SANS Livestream Alert 📣
I’m excited to announce that I’m joining Katie Nickels for the SANS Threat Analysis Rundown. We’ll discuss detection engineering, cloud security, and the latest trends in the threat landscape.
It’s on March 19 from 1pm-2pm US Eastern time. The links to view are below:
LinkedIn event link: https://www.linkedin.com/events/7305253848619618306/
YouTube:
⏪ Did you miss the previous issues? I'm sure you wouldn't, but JUST in case:
💎 Detection Engineering Gem 💎
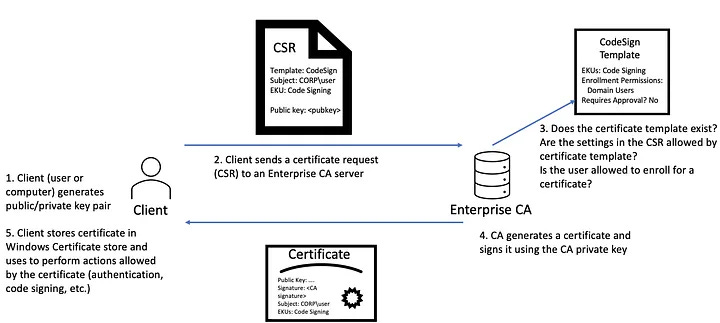
Diving Into AD CS: Exploring Some Common Error Messages by Jacques Coertze
This is an excellent, up-to-date post on how Active Directory Certificate Services (AD CS) works and doesn’t work from a red teamer perspective. Readers of this newsletter know that I am by no means a Windows expert, but I am learning a lot more reading detection engineering posts that study the Microsoft ecosystem. If you want a crash course on AD CS, this is a must-read post.
Whenever you land inside an Active Directory (AD) environment, you want to find ways to laterally move to the crown jewels: administrator accounts and AD servers. One way to do this is to abuse how the AD CS deployment is configured. There’s all sorts of snazzy tooling to help you find password hashes via Kerberoasting, but you can also use some of the techniques Coertze outlines in this research.
The cool part about examining how a red teamer succeeds or fails is the detection opportunities you find along the way. Coertze investigates 3 common error messages when trying to abuse AD CS and gives a ton of insight into how these network communications between a client, a key distribution center, and an AD server work.
The weird scenario Coertze found was when you issue an authentication request for a valid user account you control locally, you expect an NTLM password hash in response. But you can use that same certificate template, modify an attribute from client to server authentication, and request authentication for the remote DC accounts. Basically, certificate template enforcement is not a feature in some scenarios. According to Microsoft, this works as expected, and administrators must manually revoke these certificates. Classic.
🔬 State of the Art
The Cat Flap - How to really Purrsist in AWS Accounts by Michael Gschwender
So imagine you get a fancy new firewall appliance your boss says you MUST install. Maybe it’s a device from a firm that rhymes with Crisco, Dwarfinet, or something musical like Palo Soprano Networks. You download documentation, follow ALL the security recommendations, set it up, and within 30 minutes, some APT owns you. At what point is this your fault or someone else’s fault?
I often ask that question when I read blogs like this one by Gschwender that talk about cloud service providers. They are so feature-rich, which means they are ripe for abuse. So, Gschwender coins this persistence technique the “Cat Flap”. Setting up AWS Control Tower requires cross-account AdministratorAccess to a management account. But do you have a good way to memorize AWS account IDs and know which ones are legitimate and which are not? Probably not. So the beautiful thing is that you prey on victims following documentation guidelines and hope they don’t have a good way to alert them of unknown AWS Account IDs.
Not Lost in Translation: Rosetta 2 Artifacts in macOS Intrusions by Joshua Goddard
Two issues, two blogs on MacOS detection engineering and forensics! Google researcher Joshua Goddard details how MacOS uses a translation layer called Rosetta so x86/x64 binaries can run on their new ARM chips. There’s an underlying mechanism behind how these are translated to the exemplary architecture using ahead-of-time (AOT) files. These AOT files are stored as an artifact on MacOS, and SIP protects them, so you can’t modify them without booting into recovery mode. These are especially useful if you are chasing an intrusion on MacOS and the threat actor deletes a binary with subsequent AOT files for analysis.
Compromising Threat Actor Communications by Ben Folland
The point of API keys is that they should be kept secret, right? Well, maybe there’s nuance in API key security, right? For example, if you are a criminal and lazy, you buy malware that tells you to insert an API key for insta-C2 access, so you do what you are told. What you don’t know is that embedding Telegram API keys into malware is a surefire way to have a researcher pluck it out and start monitoring all your traffic.
Folland creates this process soup-to-nuts and shows receipts. If you can access malware databases, you can create clever ways to track malware families that typically have Telegram API keys inside them for C2. You can extract that API key, monitor communications to the threat actor-controlled Telegram channel, and glean additional intelligence on top of it.
RiskAnalyzer by Jerry Gamblin
Why play fun games that let you flee the everyday monotony of prioritizing vulnerabilities based on confusing equations? They don’t make you better at your job. The escapism prevents you from being a productive vulnerability data refiner. Why not practice your CVSS skills using vibe checks only?
Be a good worker-bee and try to beat me in RiskAnalyzer! Here’s my abysmal score after 10 tries. Back to refining and bringing shareholder value.
THESE WEBSITES HAVE BEEN SEIZED by seized.fyi
This cool Nascar-style website tracks criminal websites seized by law enforcement in near real-time. They have a clever way of finding seized sites under “About.” They can pick up on the sites pretty quickly, using a combination of periodically downloading ICANN’s CZDS dataset, open-source news intelligence, and checking nameservers for authoritative responses to different agencies. You can download the ~180-ish seized banners in a JSON file here.
🎙️ Detection Engineering Media
I found this podcast as a new recommendation under Spotify, so shout out to the Spotify algorithm. Reanna Schultz joins Wade Wells and Josh Mason to discuss the life of an SOC analyst, how to break into security, and how to manage the stress involved with burnout in security.
☣️ Threat Landscape
Camera off: Akira deploys ransomware via webcam by Gavin Hull, Cameron Trivella and Jon Seland
Have you secured your webcams with hardening and installed an EDR on them? I don’t think anyone has, but the Akira ransomware group may change some people’s minds. In this post, S-RM incident responders detail a security incident in which Akira gained an initial foothold into an organization, and an EDR blocked their ransomware deployment. So, they found a webcam with SMB capabilities and deployed it that way. Don’t you love the internet?
Tax season email attacks: AdWind RATs and Tycoon 2FA phishing kits by Brandon Webster
This is a great analysis of seasonal-based phishing and malware attacks over email. Malware disguised as PDFs delivering RATs sound like a TTP from 10-15 years ago, but Webster found one attacker attempting this and lured the attacker to send them an AdWind payload. I also laughed at using Cloudflare turnstiles to prevent automated analysis of a Tycoon2FA phishing kit attack.
Office of Public Affairs | Texas Man Convicted of Sabotaging his Employer’s Computer Systems and Deleting Data by U.S. Department of Justice
This is a sad (and kinda funny) press release about a malicious insider who was unfortunately laid off from his job but proceeded to backdoor the company and cause chaos. The convicted man deployed destructive code to get people locked out of Active Directory using a kill switch piece of software.
Justice Department Charges 12 Chinese Contract Hackers and Law Enforcement Officers in Global Computer Intrusion Campaigns by U.S. Department of Justice
FBI indicted 12 Chinese nationals who belong to “an ostensibly private PRC company”, i-Soon. According to the indictment, these freelance hackers work closely with the People’s Republic of China Ministry of Public Security to carry out cyber attacks against all kinds of targets. Victims include dissidents at home and abroad in the U.S. If you want a great analysis of i-Soon, which was the target of a ton of news stories last February due to a leak, check out BushidoToken’s analysis.
Update: Stopping Cybercriminals from Abusing Cobalt Strike by Cobalt Strike
This update by Fortra, who currently owns the licensing and development of Cobalt Strike, outlines their efforts to take down cracked versions of their software, and combat malicious versions in the wild. They claim that seizing and sinkholing over 200 malicious domains pointing to Cobalt Strike reduces the dwell time of infections. I’m pleased to see the effort being made here because it’s one of the best post-exploitation tools I’ve ever used, and they are doing good by helping defenders find malicious versions in the wild.
🔗 Open Source
RunAs-Stealer by DarkSpaceSecurity
PowerShell script that implements 3 different types of credential stealing techniques on Windows. This would be a great tool to deploy to test keylogging detections on your Windows hosts.
panix-v2.1.0 by Aegrah
New update for PANIX, a Linux persistence framework. They added 5 different techniques using D-Bus, Initramfs, GRUB, Polkit and Network-Manager. This is another excellent emulation and detection-testing tool for your Linux detection arsenal.
shadow-rs by joaoviictorti
shadow-rs is a Windows kernel rootkit written in Rust. Has some impressive documentation and feature sets so you can get it up and running quickly. It also has a separate crate called shadowx, essentially an API for rootkit functionality.
nanobrowser by nanobrowser
Open-source alternative to OpenAI’s Operator. It’s a chrome extension that acts as an AI web agent to automate tasks and interact with your browser session so you can get even lazier with doing work!